5 Red Team Exercises That Expose Your Real Security Gaps in 2025

Nikoloz Kokhreidze
Most security tools create a false sense of protection. Explore 5 realistic red team exercises with Notion templates that help you plan tests mirroring sophisticated attackers and identify critical vulnerabilities in your organization

I've seen it time and again throughout my career: companies spend millions on security tools but still fall victim to basic attacks. As someone who's spent over a decade in the security trenches, I can tell you that fancy dashboards don't matter if your basics aren't solid.
The truth? If you want to know your real security position, you need red team exercises that show what actually matters. I'm not talking about basic tests that scan for known bugs - I'm talking about exercises that mirror how real attackers work in 2025.
Here are five red team exercises that will show your true security gaps - the ones that lead to breaches. For each, I'll add template links later to help you plan these tests.
1. Social Engineering Campaigns: People Are Still Your Biggest Vulnerability
Let's be honest - real attackers don't try to hack your firewall when they can just trick your employees into giving up the keys.
In the real world, attackers use social engineering techniques to get initial access. They target specific employees with tailored phishing emails, calls, and even in-person tactics that get past technical controls.
A good social engineering exercise doesn't just test if people click links. It copies multi-stage campaigns that match actual threat actor behavior. This includes research on key employees, creating real-looking scenarios, and using triggers that work even on security-aware staff.
What you'll learn: This test shows if your security training leads to better decisions in real situations. You'll see which departments are most at risk, what tactics work against your organization, and how well your controls catch good phishing attempts.
2. Privileged Credential Attacks: The Path From Entry to Domain Admin
Almost every major breach follows this pattern: attackers get initial access, then move until they get privileged credentials that give them the keys to your kingdom.
Your red team should test how they can move from an initial foothold (like a hacked workstation) to getting domain admin rights or cloud privileges. This test focuses on credential theft, privilege escalation, and moving through your network.
Recent research shows identity-based attacks have jumped as attackers focus on cloud systems. Once they have credentials, moving through your network becomes easy.
What you'll learn: You'll find out if your security can detect credential theft tools, whether your admin accounts have too many permissions, and if your network setup stops attackers from moving around. Most important, you'll see if you can spot the subtle signs of someone quietly gaining higher access.
3. Cloud Misconfiguration Exploits: Your Most Accessible Attack Surface
Your cloud systems likely have dangerous gaps that normal security tools can't see. This exercise finds and uses common cloud setup mistakes that give attackers easy wins.
The test should check for exposed storage, overly open permissions, unprotected APIs, and serverless function flaws. As a recent Forbes article noted, a single mistake—often just an overly open permission or exposed storage—can ruin everything.
The red team should try to find resources open to the public, gain higher privileges in cloud systems, and move between different cloud services to access sensitive data.
What you'll learn: This exercise shows blind spots in your cloud security that automated tools often miss. You'll find out if your cloud security is set up right, where your sensitive data is most exposed, and whether you can detect unusual access patterns.
4. Supply Chain Compromise Simulations: You're Only as Secure as Your Weakest Vendor
Today's companies rely on dozens or hundreds of outside vendors, creating a huge attack surface you don't directly control. Supply chain attacks have become one of the most effective ways for smart attackers to breach well-protected organizations.
In this test, your team copies attacks that use your supply chain - including software dependencies, vendor access, and update systems. They'll try to find trusted relationships that could be used against you and test how well you can detect compromised vendor systems or bad updates.
These attacks can lead to severe problems including money loss, data breaches, lost trust, and even national security risks.
What you'll learn: This test helps you understand which third-party connections pose the greatest risk, whether your vendor risk program works, and if you can detect strange behavior from trusted outside sources. You'll also learn if your incident response plan covers supply chain attacks.
5. Defensive Control Evasion: Testing Your Actual Detection Capabilities
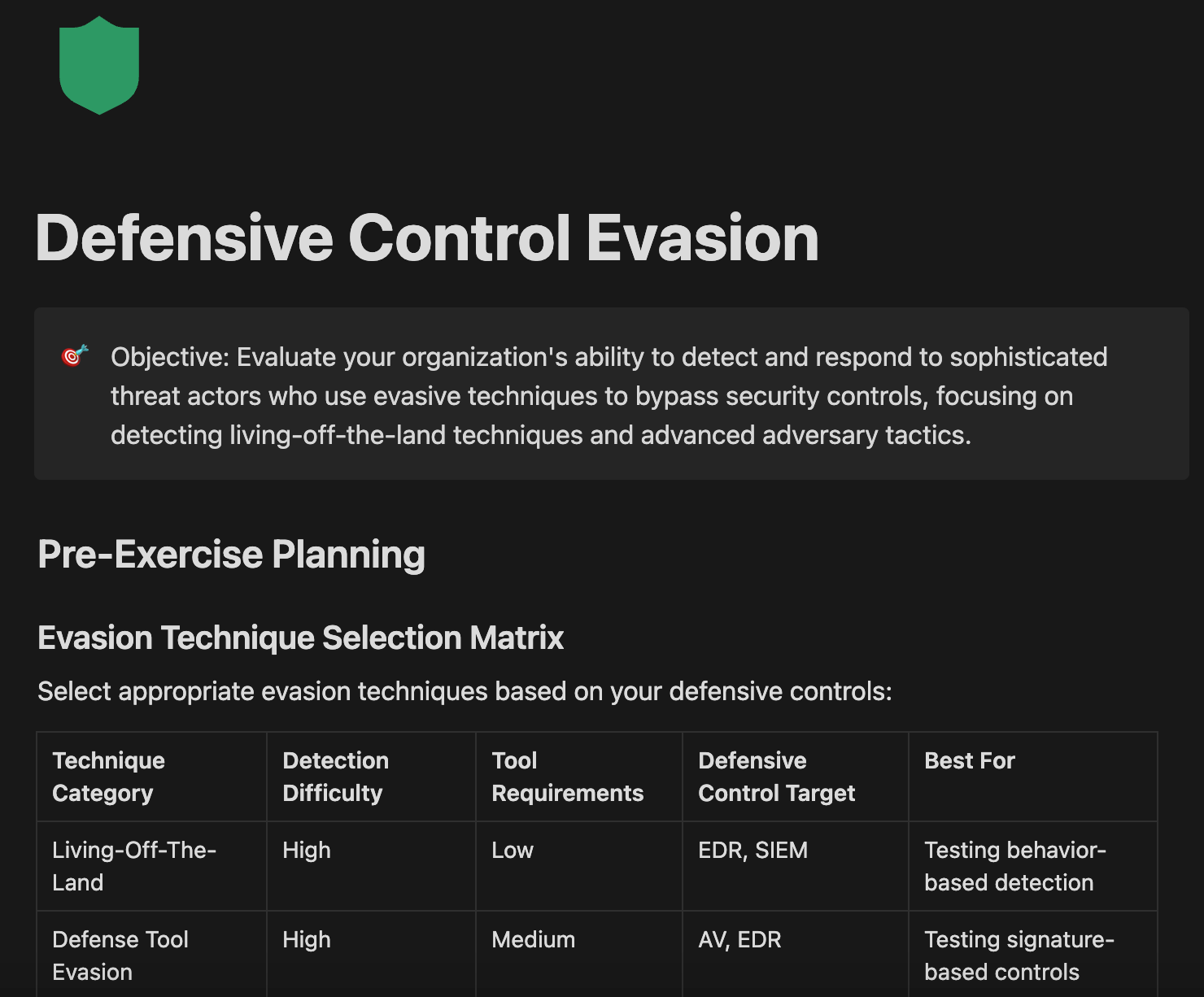
Modern attackers don't use noisy malware that triggers alarms - they use quiet techniques designed to blend in with normal activity. This test checks whether your security team can spot sophisticated threats that try to stay hidden.
Your red team should use living-off-the-land techniques, fileless malware, and evasion tactics that copy advanced persistent threats. Rather than setting off obvious alarms, they should try to accomplish their goals while staying under the radar.
Security experts note that using built-in system tools is exactly how hackers stay undetected, sometimes for months.
What you'll learn: This test reveals if your security team can tell the difference between normal system behavior and malicious activity, if your endpoint protection catches fileless attacks, and whether your security tools work together as a system. You'll also see how quickly your team responds to subtle signs of compromise.
Moving Beyond the Checklist Approach to Security
These five exercises will tell you more about your security position than any compliance checklist or scanning tool. They focus on attack patterns that actually lead to breaches, not theoretical problems that look good in reports but don't reflect real risk.
The most valuable outcome isn't just finding vulnerabilities - it's understanding the full attack chain and how multiple small weaknesses can combine into major problems. This complete view lets you make strategic security investments rather than quick fixes.
If you haven't run these types of realistic tests, you don't truly know your security status. And in today's threat landscape, that's a risk no organization can afford.
What red team exercises have provided the most value for your organization? I'd love to hear about your experiences in the comments below.



