The Fractional CISO and Strategic Advisory for B2B scaleups. We anchor your growth in foundational trust and engineer the cyber resilience that protects your enterprise value. We provide the executive oversight needed to navigate board-level scrutiny and satisfy global compliance demands.
Clear business outcomes for every stakeholder, not just security for security's sake.

Fractional CISO & Strategic Advisor
With over 13 years of experience at the high-stakes intersection of cybersecurity and business strategy, I serve as a strategic thought partner to B2B scaleups. Having built security programs for Forbes Cloud 100 FinTech, Banking, Finance, and FMCG leaders and reviewed over 150+ B2B security programs, I translate technical complexity into business resilience and investor trust.
Enabled €150M+ in acquisitions by ensuring security programs exceed the most rigorous international due diligence. I prepare founders for the "security hurdle" in Tier-1 exits.
Identified and recovered €35M in savings through intelligent tool consolidation and risk-aligned roadmaps, proving that robust security can increase, not drain, your bottom line.
Providing elite, cross-border security oversight for high-growth technology firms scaling across EMEA and North America, bridging the gap between European regulation (NIS2) and US market expectations (SOC 2).
Maintained a 100% first-time pass rate on ISO 27001 and SOC 2 audits. I deliver audit-ready frameworks that satisfy global enterprise procurement without the traditional "enterprise bloat."
For high-growth B2B companies, security is no longer a technical checkbox, it is a fundamental driver of enterprise value.
We don't just "do" security; we integrate it into your business strategy to unlock new markets and protect your enterprise value.
A structured, 4-stage executive engagement designed to align your security posture with your business growth milestones and investor expectations.
Week 0–4
Executive Risk Audit
Identifying sales friction, valuation risks, and compliance gaps. We align security with your 12-month business objectives.
Immediate Executive Visibility
Month 2–6
Infrastructure & Trust
Building the "Language of Trust" required to win 7-figure global deals while ensuring AI and product innovation remain secure.
Accelerate Global Deals
Month 4–8
Audit & Global Compliance
Achieving third-party verification to satisfy international regulators and enterprise procurement teams with zero downtime.
Institutional Trust Achieved
Month 7+
Strategic CISO Leadership
Ongoing fiduciary oversight, protecting your valuation through M&A, and providing independent risk reporting to your Board.
Protect Enterprise Value
We tailor this roadmap to your specific exit strategy or scaling goals: whether you’re preparing for an expansion, a Series B funding round, mergers & acquisitions, or long-term market dominance.
Choose the engagement level that matches your current business stage and strategic goals.
Unblock a specific security challenge or deal-breaker in a single session.
60-minute targeted consultation
Secure a long-term strategic partner to lead your security program and unblock enterprise revenue.
30-min strategy & scoping call
Access the tools and frameworks I use to lead world-class security programs.
The Mandos methodology
Strategic questions? Direct Inquiry
My insights on what's actually broken in cybersecurity and how to fix it.

Stop losing million-euro enterprise deals: learn the brutal truth about how a vCISO rapidly accelerates sales and achieves ISO 27001 by focusing only on what truly closes deals.
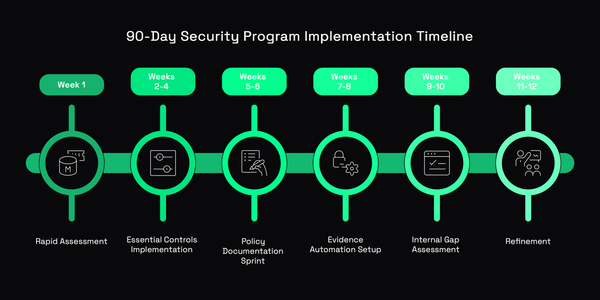
Build an ISO 27001 and SOC 2-aligned security program in 90 days to win enterprise deals. Practical guide for founders and CTOs with limited time.
Fractional CISO services are essential for growing B2B companies to win enterprise customers and grow with confidence. In this article we look at what is fractional CISO, how it works and associated costs.
Most growing B2B companies are making the same expensive mistake with AI that they made with cloud computing 15 years ago. Here's why building your own AI infrastructure will kill your competitive advantage and what smart leaders are doing instead.
The Model Context Protocol lets AI access multiple systems simultaneously, creating security risks most organizations aren't prepared for. Learn the strategic framework needed for proper MCP governance.

Unlock your leadership potential in cybersecurity. Learn to communicate business value, build strategic networks, and embrace mentorship to bridge the gap between technical expertise and executive roles.