Real insights on building security programs that accelerate growth instead of slowing it down
Don't fall behind - Mandos subscribers are already implementing these strategies

Stop losing million-euro enterprise deals: learn the brutal truth about how a vCISO rapidly accelerates sales and achieves ISO 27001 by focusing only on what truly closes deals.
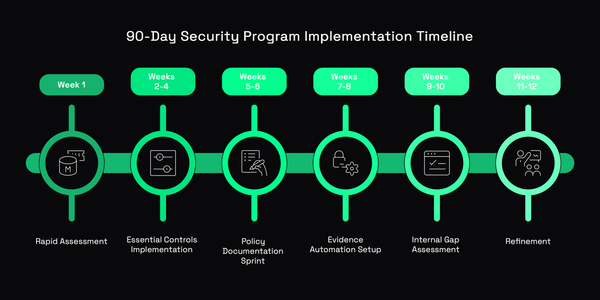
Build an ISO 27001 and SOC 2-aligned security program in 90 days to win enterprise deals. Practical guide for founders and CTOs with limited time.
Fractional CISO services are essential for growing B2B companies to win enterprise customers and grow with confidence. In this article we look at what is fractional CISO, how it works and associated costs.

Most B2B companies build cybersecurity programs backwards - starting with compliance instead of real security. Learn why this approach fails and how fractional CISO services can help you build effective security that actually prevents breaches while achieving compliance.

Most growing B2B companies make a critical mistake: they treat cybersecurity as a technical problem instead of business protection. Here's how strategic cybersecurity leadership changes everything.
Most growing B2B companies are making the same expensive mistake with AI that they made with cloud computing 15 years ago. Here's why building your own AI infrastructure will kill your competitive advantage and what smart leaders are doing instead.

Stop choosing between ideal security and operational constraints. Learn how to implement a staged security roadmap that bridges the gap between legacy systems and modern protection standards.

Your security team is spending 70% of their time chasing ghosts. Here's how to reclaim those hours for strategic work that actually matters.

Security teams have surrendered autonomy to vendors. AI is democratizing development across security teams. Learn how to rebuild your engineering capabilities without hiring an army of coders.