Practical insights at the intersection of AI, cybersecurity, and leadership
Don't fall behind — Mandos subscribers are already implementing these strategies

Stop choosing between ideal security and operational constraints. Learn how to implement a staged security roadmap that bridges the gap between legacy systems and modern protection standards.

Your security team is spending 70% of their time chasing ghosts. Here's how to reclaim those hours for strategic work that actually matters.

Security teams have surrendered autonomy to vendors. AI is democratizing development across security teams. Learn how to rebuild your engineering capabilities without hiring an army of coders.

Most security tools create a false sense of protection. Explore 5 realistic red team exercises with Notion templates that help you plan tests mirroring sophisticated attackers and identify critical vulnerabilities in your organization
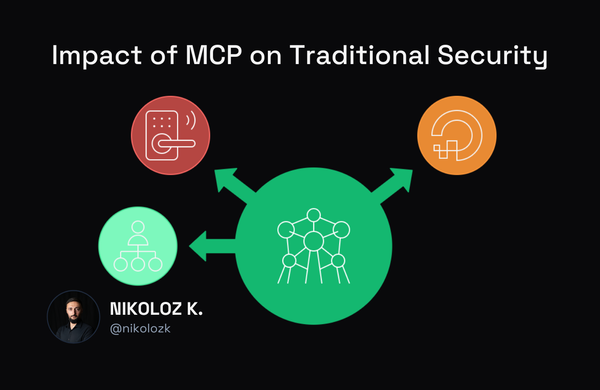
The Model Context Protocol lets AI access multiple systems simultaneously, creating security risks most organizations aren't prepared for. Learn the strategic framework needed for proper MCP governance.
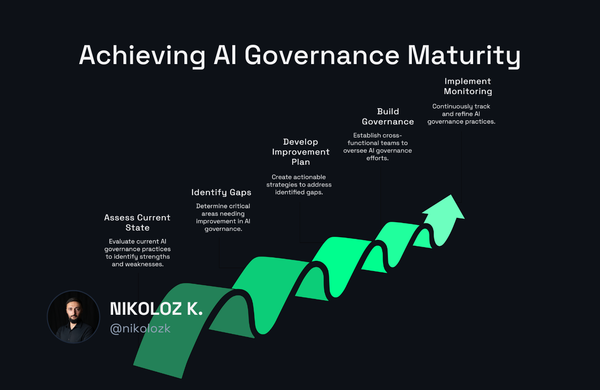
Traditional security fails with AI systems. Discover Microsoft's RAI Maturity Model and practical steps to advance from Level 1 to Level 5 in AI security governance.

Cybersecurity imposter syndrome is practically universal among leaders. Learn how deliberate failure builds genuine confidence no certification provides.

Three powerful AI tools enable analysts to automate complex binary analysis. See how security teams can reverse engineer without additional headcount.
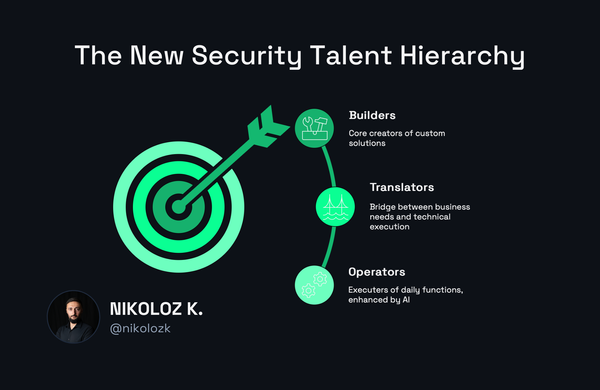
The vendor dependency trap is crippling security teams. AI is democratizing building capabilities that were once vendor-exclusive. Develop these five critical skills now before your competitors do.