The Builder Strikes Back: How Security Teams Must Reclaim Their Engineering Edge

Nikoloz Kokhreidze
The vendor dependency trap is crippling security teams. AI is democratizing building capabilities that were once vendor-exclusive. Develop these five critical skills now before your competitors do.
The Vendor Dependency Trap We've All Fallen Into
Security teams have been slowly surrendering their technical sovereignty for over a decade. What started as a pragmatic response to cloud migration has evolved into a crippling dependency on vendor ecosystems. The modern security department has transformed from builders to buyers, from creators to consumers, from engineers to administrators.
Look around your security team. How many true builders do you have? Not people who can configure a SIEM or tune an EDR—actual engineers who can create solutions from scratch when nothing on the market fits your needs. For most organizations, that number hovers dangerously close to zero.
This isn't accidental. The SaaS revolution promised to free security teams from infrastructure management so they could focus on "more strategic work." But what actually happened? We traded infrastructure management for vendor management—endless procurement cycles, integration challenges, and budget battles that consume more time than the technical problems they supposedly solve.
The result is security teams staffed with specialists who know vendor platforms but lack fundamental building skills. We've created security departments full of people who can tell you every feature of CrowdStrike or SentinelOne but couldn't write a basic detection algorithm if the pre-built ones fail. Teams that can recite security policies but can't automate their own GRC workflows when commercial tools fall short.
This overweight vendor dependency has quietly become our industry's Achilles' heel—and the ongoing AI revolution is about to expose it.
The AI Inflection Point That Changes Everything
The emergence of AI represents the most significant shift in security capabilities since cloud computing. But unlike cloud, which centralized power in the hands of vendors, AI is democratizing the ability to build and create—putting power back into the hands of security teams willing to seize it.
Through capabilities like tool calling, agents, and API integration, AI is collapsing the technical barriers that once made custom development prohibitively expensive for most security teams. Tasks that once required weeks of engineering effort can now be accomplished in hours. Integration challenges that demanded specialized knowledge can now be solved through conversational interfaces with AI assistants (albeit with its own downsides).
This isn't theoretical—it's happening right now in front of our eyes. Security teams with building capabilities are already using AI to create custom detection/response automations for their unique needs that outperform vendor solutions at a fraction of the cost. They're automating GRC processes that vendors claim require expensive modules. And they're also building bespoke security tools tailored precisely to their organization's unique threat landscape instead of accepting the one-size-fits-all approaches that dominate the commercial market.
The implications are profound: the competitive advantage in security is shifting from those who can buy the best tools to those who can build the best tools. And most security teams are dangerously unprepared for this shift.
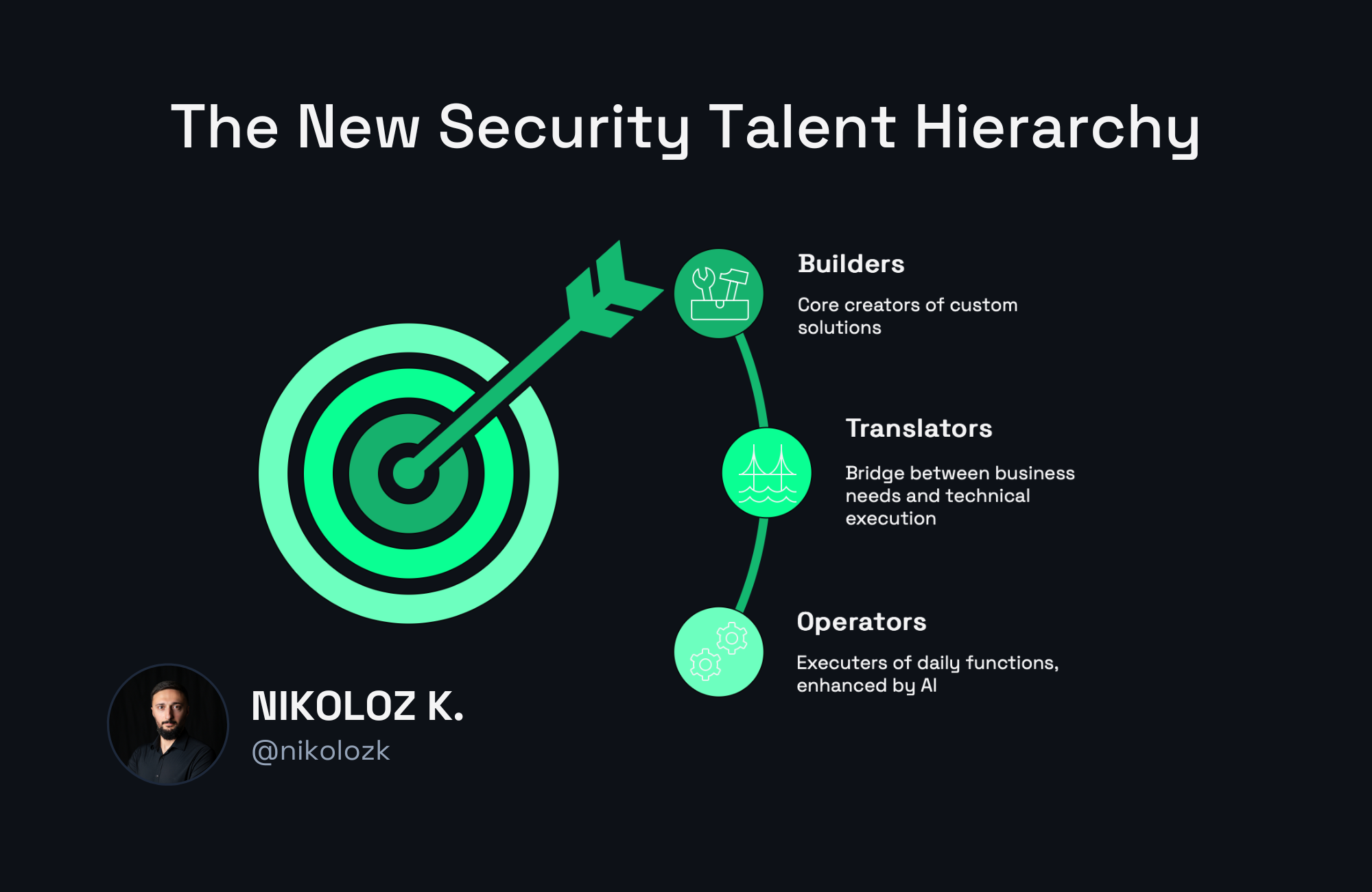
The New Security Talent Hierarchy
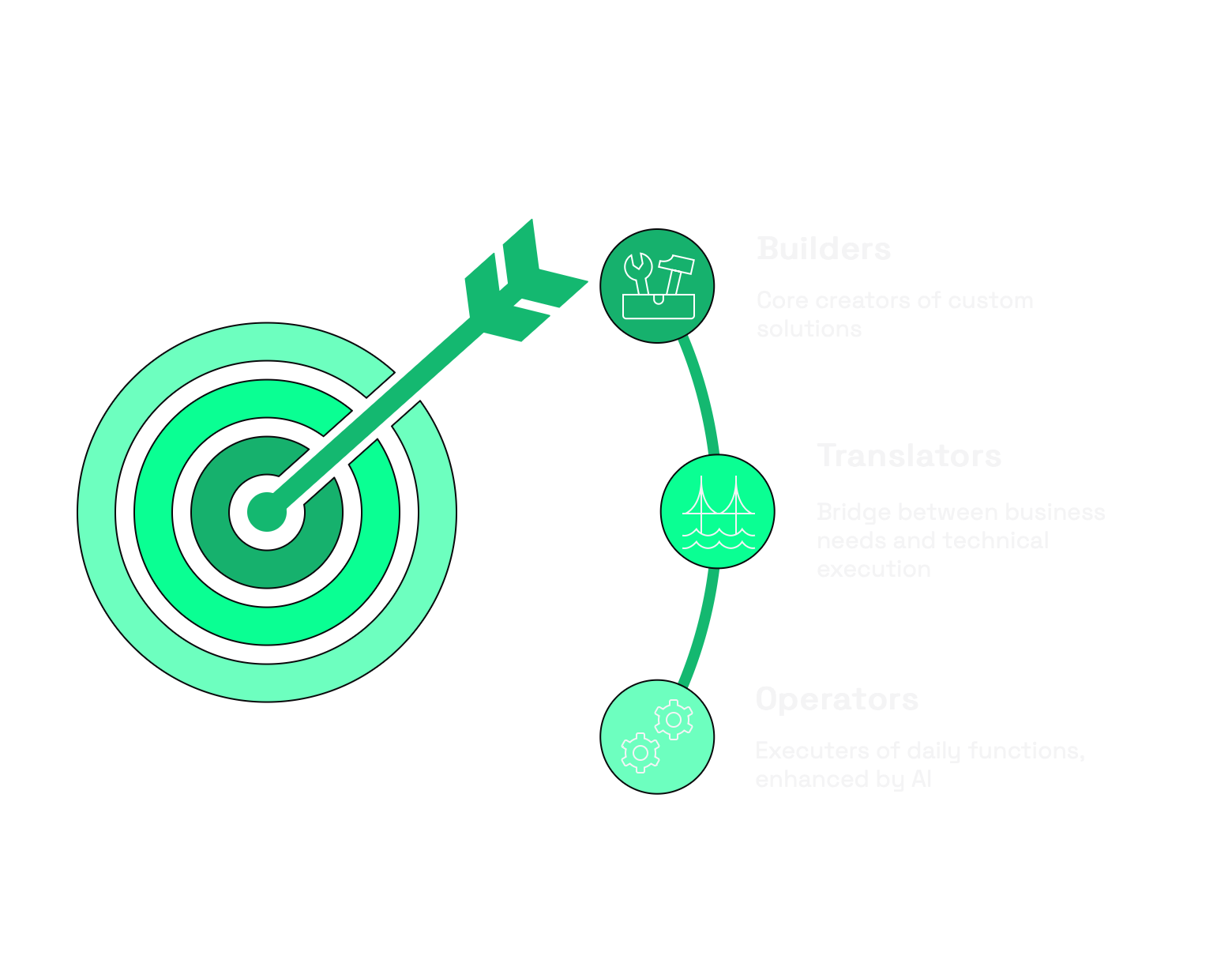
The AI revolution is creating a new talent hierarchy in security that will reshape team structures and career trajectories:
- Builders will sit at the top—professionals who can create custom solutions, integrate various systems, and automate complex workflows using AI as a force multiplier. Their value will skyrocket as organizations realize the competitive advantage of custom-built security capabilities.
- Translators will form the crucial middle layer—those who can translate business and security requirements into specifications that builders and AI can execute against. They'll bridge the gap between technical possibilities and business needs.
- Operators will remain essential but increasingly augmented—those who execute daily security functions will find their roles enhanced by AI but will need to develop adjacent building skills to maintain their value.
This hierarchy represents a fundamental inversion of how many security teams currently operate, where technical builders are often undervalued compared to policy experts, compliance specialists, and vendor relationship managers.
The most dangerous position in this new hierarchy? The pure specialist who can neither build nor translate—the compliance expert who can't automate workflows, the threat analyst who can't create detection algorithms, the security architect who can't integrate systems. These roles won't disappear overnight, but their leverage and compensation will steadily erode as AI makes their specialized knowledge more accessible to those with building skills.
The Building Skills Gap Is Worse Than You Think
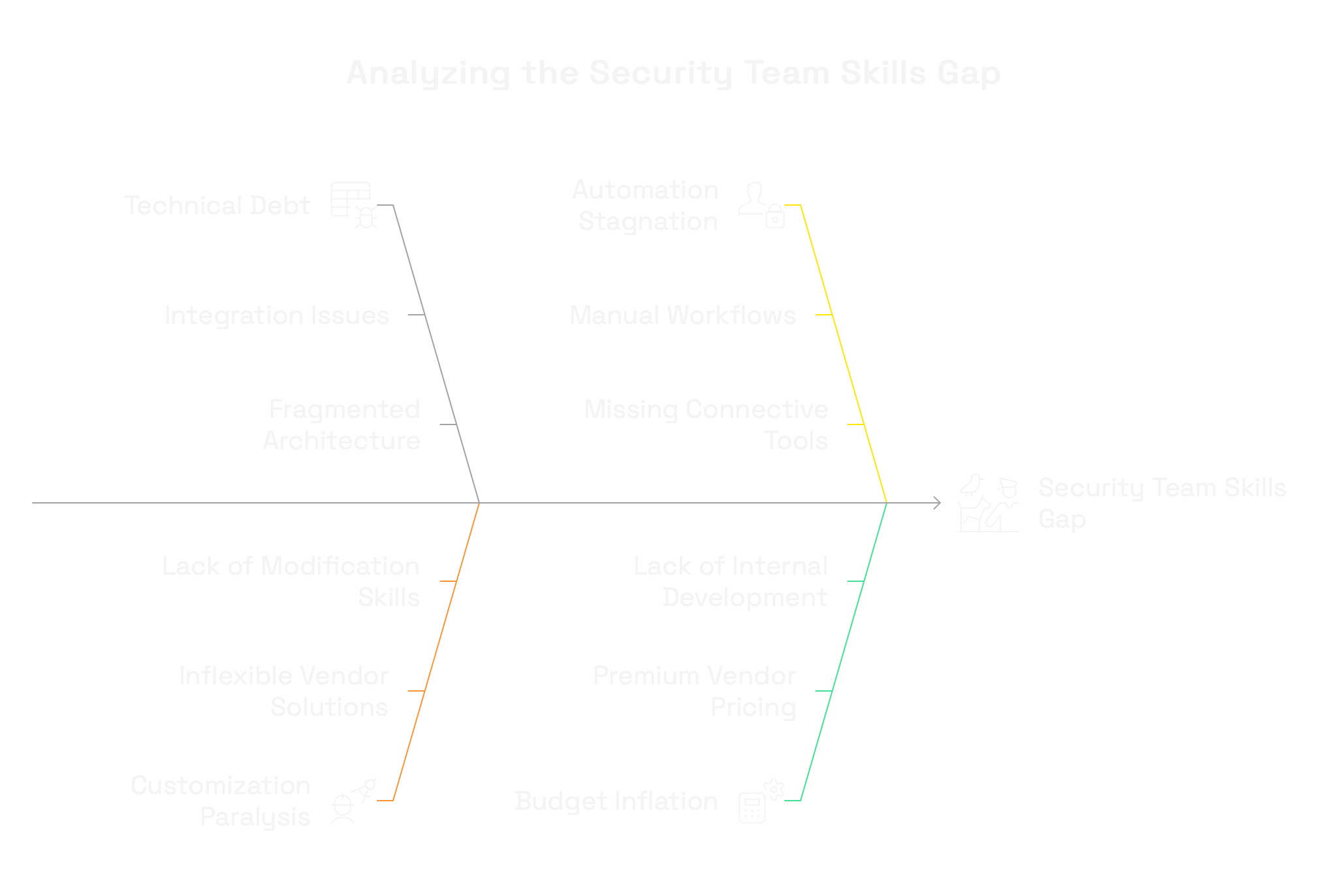
The most security teams have systematically eliminated building capabilities from their talent pool. In the rush to adopt vendor solutions, they've optimized for professionals who can implement and operate commercial tools rather than create new ones.
This building skills gap manifests in several critical ways:
- Technical debt accumulation: Security teams struggle to integrate disparate vendor solutions, creating fragmented architectures held together by manual processes and spreadsheets.
- Customization paralysis: When vendor solutions don't quite fit business requirements, teams lack the capability to extend or modify them, leading to suboptimal security controls.
- Automation stagnation: Critical security workflows remain manual because teams can't build the connective tissue between systems that vendors don't prioritize.
- Budget inflation: Organizations pay premium prices for vendor features they could build internally at a fraction of the cost with the right talent.
The most alarming aspect of this skills gap is how invisible it remains to many security leaders. They've accepted vendor dependency as the natural state of security operations rather than recognizing it as a strategic vulnerability that limits their team's effectiveness.
The Five Building Capabilities Every Security Team Needs Now
To thrive in the AI era, security teams must develop five critical building capabilities:
- Programmatic thinking: The ability to break complex security problems into logical components that can be solved systematically—whether through code, configuration, or AI prompting.
- API fluency: Understanding how to leverage APIs to create integrations between systems, automate workflows, and extend vendor capabilities beyond their out-of-box limitations.
- Data manipulation: Skills to transform, normalize, and analyze security data across disparate formats and structures to derive actionable insights beyond what vendor analytics provide.
- Automation design: The capability to identify repetitive security processes and create automated workflows that reduce manual effort while improving consistency and coverage.
- AI orchestration: Expertise in directing AI tools to perform complex security tasks through effective prompting, tool calling, and output validation.
These capabilities don't require every security professional to become a software engineer. But they do require a fundamental shift in mindset from consumption to creation, from dependence to self-sufficiency.
The organizations that develop these capabilities will gain an immeasurable advantage: they'll implement security controls faster, respond to threats more effectively, and operate at a fraction of the cost compared to bloated teams that remain dependent on vendor roadmaps and release cycles.
How to Transform Your Team from Consumers to Creators
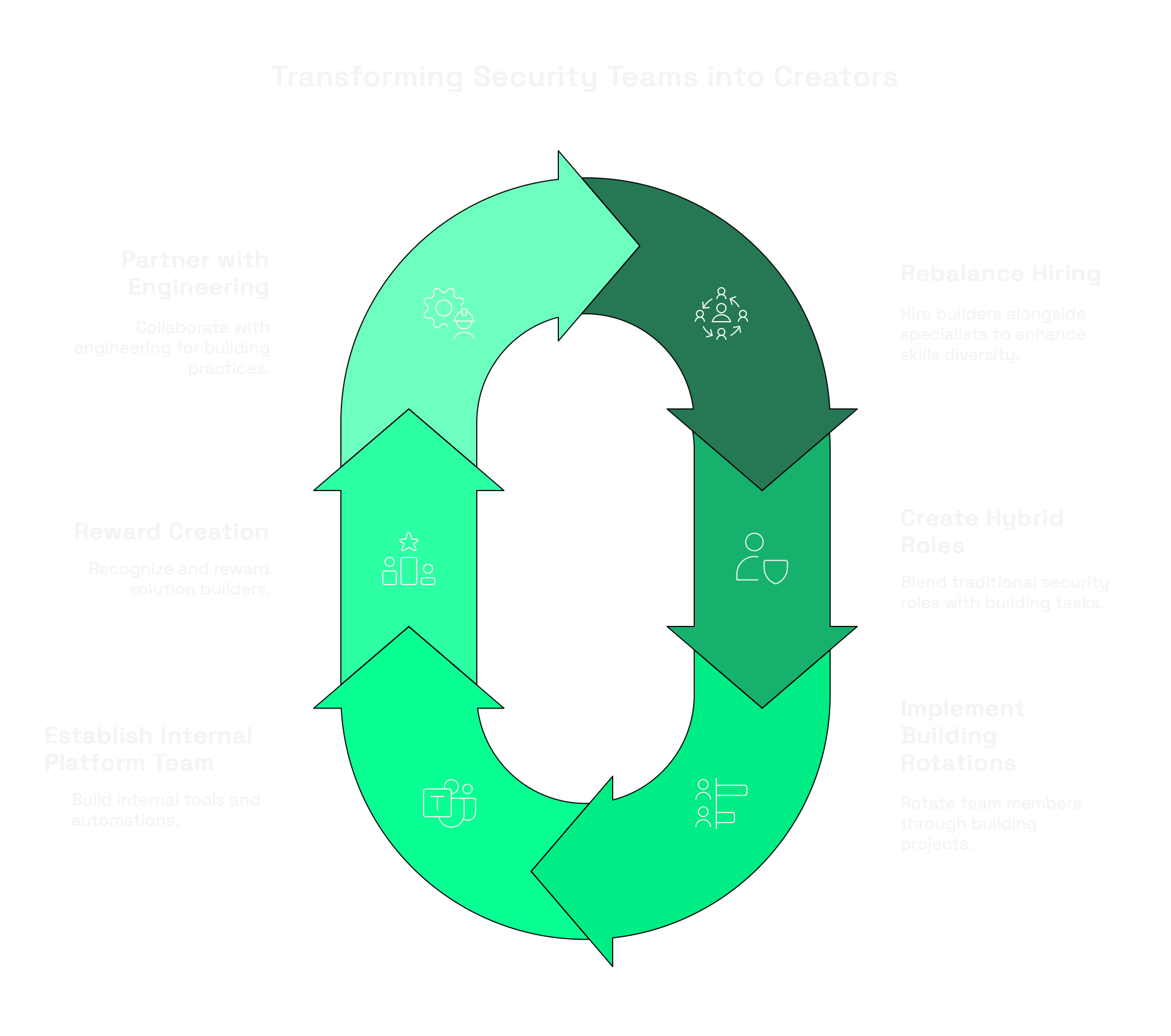
Rebuilding your security team's creation capabilities requires deliberate action across hiring, training, and organizational structure:
- Rebalance your hiring profile: For every three specialists you hire, add one builder with strong programming, integration, and automation skills—even if they lack traditional security backgrounds.
- Create hybrid roles: Establish positions that blend traditional security domains with building responsibilities. Your GRC analyst should also automate compliance workflows; your threat hunter should also build detection algorithms.
- Implement building rotations: Require every security team member to spend time working directly with builders on integration and automation projects to develop adjacent skills.
- Establish an internal security platform team: Create a dedicated function responsible for building internal tools, automations, and integrations that vendors don't provide.
- Reward creation over consumption: Modify your performance metrics to recognize and reward team members who build solutions rather than just effectively operating vendor tools.
- Partner with engineering: Forge stronger relationships with software engineering teams to share building practices, tools, and potentially resources.
The most effective approach combines these strategies with a clear message: in the AI era, building is no longer optional—it's a core security function that determines your team's effectiveness, efficiency, and ultimately its survival.
Managing Vendor Relationships in the Builder Era
As your team develops stronger building capabilities, your vendor relationships will fundamentally change—and vendors won't like it. You'll shift from being a passive consumer to an active co-creator who:
- Demands open APIs and extensibility as non-negotiable requirements in procurement
- Builds around vendor limitations rather than waiting for roadmap promises
- Creates competitive leverage by maintaining the ability to replace vendors who don't deliver value
- Negotiates from strength with a clear understanding of build-versus-buy economics
This shift will create tension. Vendors have built business models around customer dependency and will resist your move toward self-sufficiency. They'll claim their proprietary approaches are superior to anything you could build. They'll warn about support issues for custom integrations. They'll emphasize compliance risks of non-standard implementations.
Stand firm. The vendors worth keeping will adapt to this new reality, embracing their role as platforms that amplify your team's building capabilities rather than replacing them. The rest will reveal themselves as dependencies you're better off without.
Don't get me wrong. Most great innovations in our industry come from established vendors and startups who are changing the status quo—companies like Wiz and many others. Without them many organizations would have failed long time ago and those who think they can solve problems just by building internally are delusional.
We need vendors and solution providers; they are our best partners in solving big, complex problems. But the truth is that the niche problems unique to your organization are often more painful than the big, common problems vendors solve. This is where building internally becomes the differentiator between successful and failed security teams.
The Bottom Line: Build or Be Left Behind
The security industry stands at an inflection point. AI is democratizing the ability to build, integrate, and automate security capabilities that were once the exclusive domain of vendors or specialized engineering teams.
Security leaders face a clear choice: develop building capabilities within their teams or accept a future of perpetual vendor dependency, escalating costs, and competitive disadvantage.
The most successful security organizations of the next decade won't be those with the biggest budgets or the most comprehensive vendor portfolios. They'll be those that combine deep security expertise with the ability to build precisely what they need when they need it—leveraging AI as the ultimate force multiplier for human creativity and problem-solving.
The question isn't whether your security team needs building capabilities—it's whether you'll develop them before your competitors do.
Before you go
If you found this article useful, I'd really appreciate if you could forward it to your community and share your feedback below.
For more frequent cybersecurity leadership insights and tips, follow me on LinkedIn, BlueSky and Mastodon.
Best,
Nikoloz



