5 AI Agent Types Modern Security Teams Must Know About

Nikoloz Kokhreidze
I've decoded the AI agent types that are revolutionizing enterprise cybersecurity programs. Are you leveraging all five? Discover which ones your security team is missing and how you can use them for your advantage.

Behind every successful cybersecurity system or information security program there will be an AI agent.
A system designed to perceive their environment and take actions to achieve specific outcomes.
But not all AI agents are created equal.
In this post I will guide you through the five most crucial types of AI agents and help you understand their application in cybersecurity.
Let's start with the most basic one.
Simple Reflex Agents
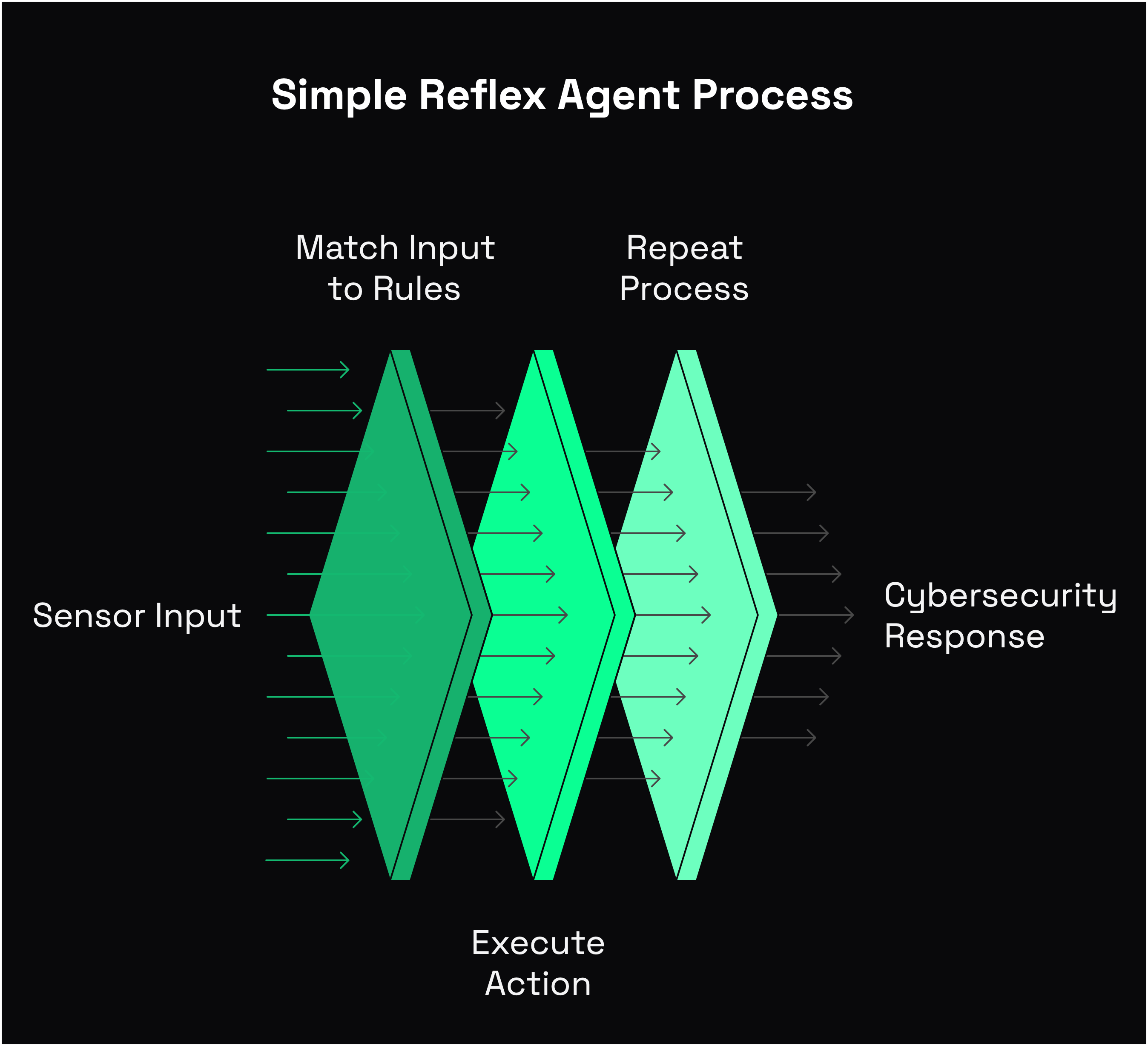
Simple reflex agents represent the most basic form of artificial intelligence. They follow basic rules without thinking about the long-term effects of what they do. Remember 5 years ago when every EDR/SIEM provider was selling products with "AI" slapped on it? This is it, if-else statements on steroids.
How They Work
The architecture of a simple reflex agent follows this basic flow:
- Receive input from sensors/environment
- Match the current input to predefined rules
- Execute the corresponding action
- Repeat
In security contexts, simple reflex agents power:
- Signature-based antivirus software that identifies known malware patterns and immediately quarantines matching files
- Basic firewall rules that block traffic from specific IP addresses or ports
- Simple intrusion detection systems that trigger alerts when they detect predefined attack patterns
Limitations in Security Contexts
While it might be useful as a first line of defense, simple reflex agents suffer from significant limitations:
- They can only detect known threats with exact matching patterns
- They cannot adapt to new attack vectors without manual rule updates
- They generate high rates of false positives in complex environments
- They're easily circumvented by slight variations in attack methods.
It's like a basic WAF that triggers an alert when it detects a special character like in request header. Provide a combination or encoded characters and your "AI powered WAF" will be bypassed. It does not analyze patterns over time, or consider the context of the activity.
The next AI agent might be a bit more interesting.
Is Security Blocking Your Next Enterprise Deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
Model-Based Reflex AI Agents
Model-based agents are capable of maintaining an internal representation (model) of the world. This allows them to track the state of their environment even when it's not observable at any single moment.
How They Work
Model-based agents:
- Maintain an internal state that represents the world
- Update this state based on new perceptions
- Consult transition models to understand how the world evolves
- Use condition-action rules based on the current state (not just current perception)
In security, model-based agents can enable:
- Network behavior analysis systems that maintain models of "normal" network states and flag deviations
- Stateful inspection firewalls that track the status of active connections
- Context-aware security tools that consider the relationship between different events
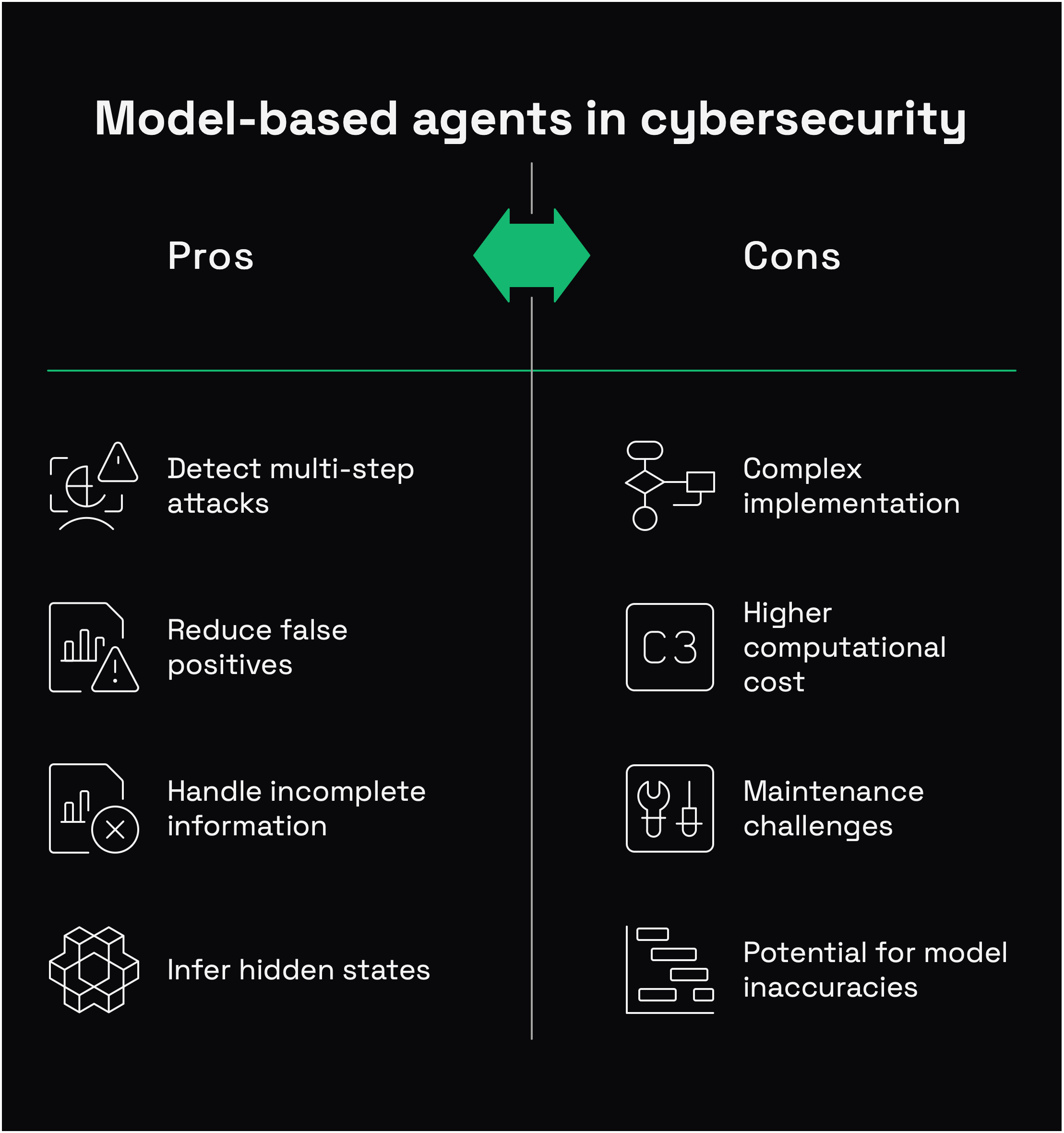
Model-based agents offer significant improvements for security applications:
- They can detect multi-step attacks by maintaining state
- They reduce false positives by considering context
- They function with incomplete information
- They can even infer hidden states based on partial observations
One example of a model-based security agent is an impossible travel tracking. Unlike a simple reflex agent that only flags individual suspicious logins, this system maintains a model of user behavior patterns. So, it can detect when someone attempts to log in from an unusual location shortly after a successful login from a different continent.
Now, what if AI agents could take actions to achieve goals?
Is Security Blocking Your Next Enterprise Deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
Goal-Based Agents
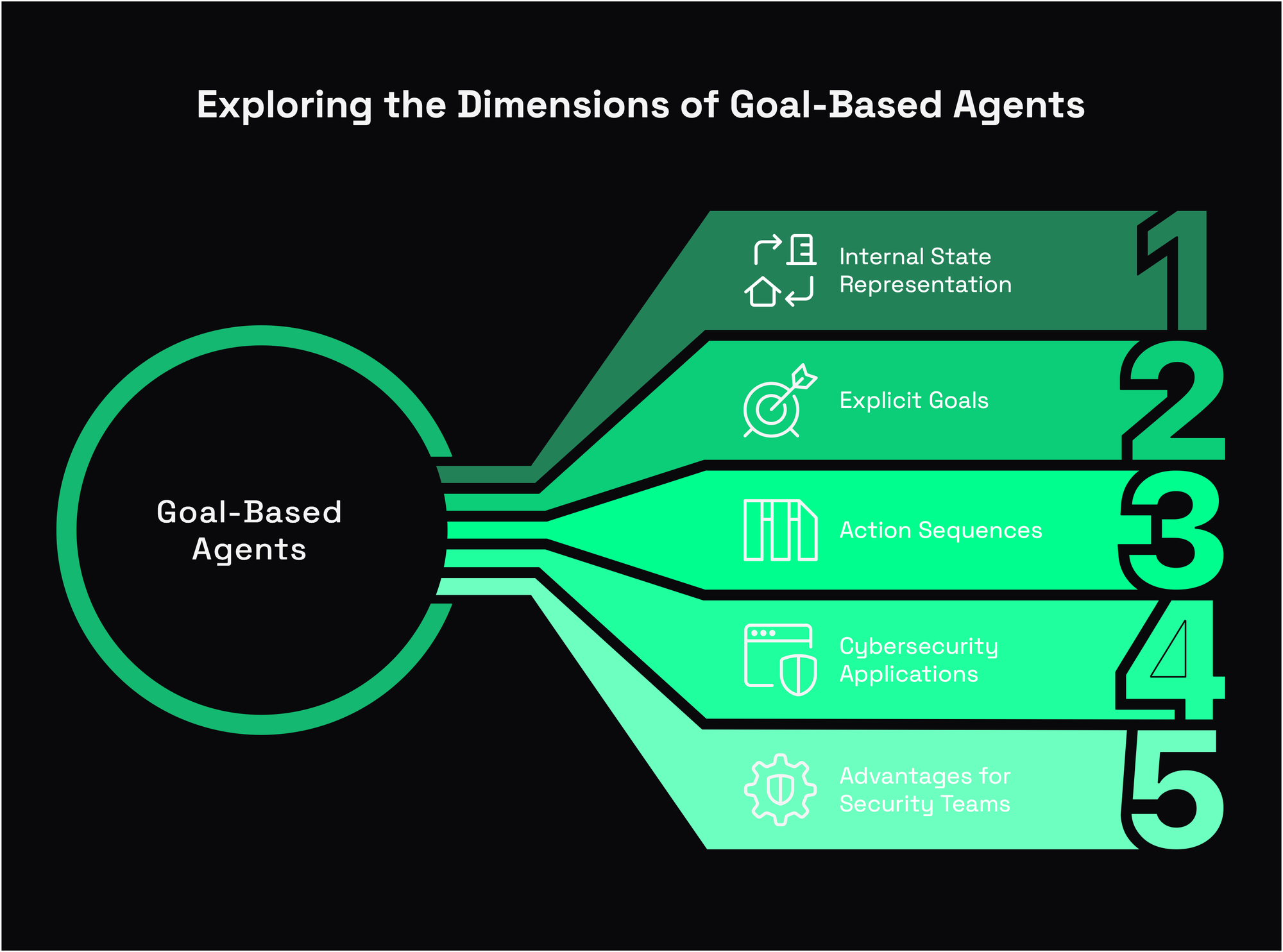
Goal-based agents take intelligence a step further by considering desired outcomes. Instead of just reacting to the environment based on rules (boring and outdated), they actively plan sequences of actions to achieve specific goals.
How They Work
These agents:
- Maintain an internal state representation
- Define explicit goals
- Consider different possible action sequences
- Choose actions that move toward goal states
In security operations, goal-based agents can play a huge roal:
- Security orchestration and automated response (SOAR) platforms that work toward specific security objectives
- Penetration testing tools that systematically probe for weaknesses to achieve the goal of identifying vulnerabilities
- Automated incident response systems that work toward the goal of containing threats
Goal-based agents provide critical capabilities to security teams:
- They can proactively identify paths to security breaches before attackers do
- They can balance multiple security objectives simultaneously
- They adapt to changing environments by finding new paths to their goals
- They provide logical justifications for their actions (the path to the goal)
Imagine an automated IR system that receives an alert about potential data exfiltration. Rather than simply blocking the specific connection (a reflex action), a goal-based agent would establish the goal of "contain the threat while preserving evidence for investigation." To achive this, it might isolate the affected system, capture network traffic and create memory dumps. All actions chosen specifically to achieve the defined goal.
The following AI agent adds some more spice to goal setting.
Utility-Based Agent
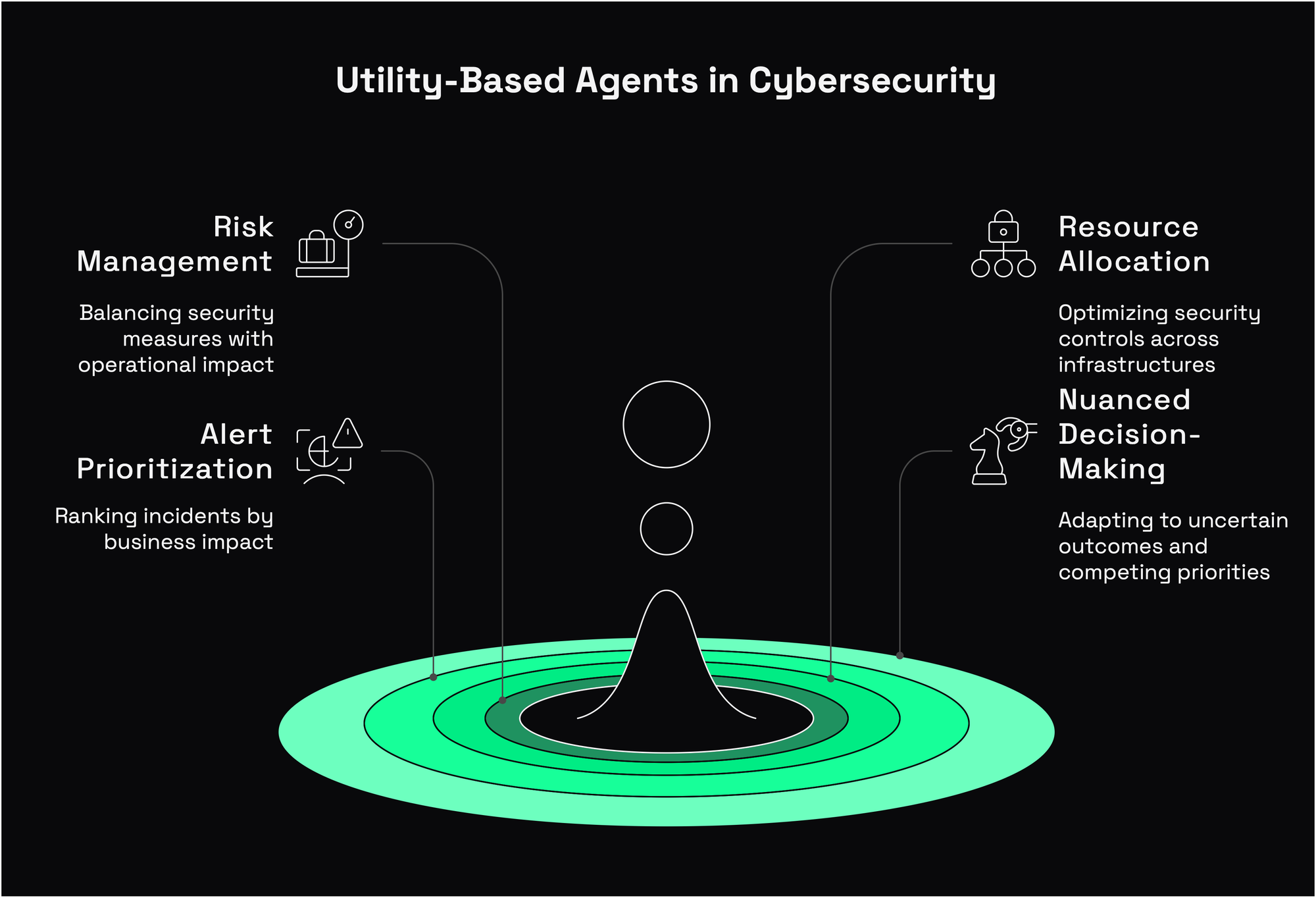
Utility-based agents refine the goal-based approach by adding a critical capability. They can check and compare the desirability of different states or outcomes. Instead of seeing the world in black and white (goal achieved or not achieved), they operate on a spectrum of preference.
How They Work
These sophisticated agents:
- Maintain an internal state representation
- Check different possible outcomes using a utility function
- Calculate the expected utility of various action sequences
- Choose actions that maximize expected utility
Utility-based reasoning enables:
- Risk management frameworks that balance security measures against operational impact
- Resource allocation systems that optimize deployment of security controls across complex infrastructures
- Alert prioritization engines that rank incidents based on potential business impact
In security operations, utility-based agents shine because:
- They can make optimal decisions when facing uncertain outcomes
- They balance competing priorities (security vs. usability vs. cost)
- They adapt to changing risk appetites by adjusting utility functions
- They handle scenarios where perfect security is impossible or impractical
A utility-based security agent might manage access control during a suspected breach. If goal-based agent would lock down all systems, the utility-based agent will first calculate the utility of various response levels.
For example: it might determine that completely locking critical healthcare systems carries extreme negative utility (potential loss of life), while the utility loss from potential data theft is lower. It would then implement graduated controls that maximize overall utility—perhaps implementing additional authentication steps rather than a complete lockdown.
The next AI agent is my personal favorite.
Learning Agents
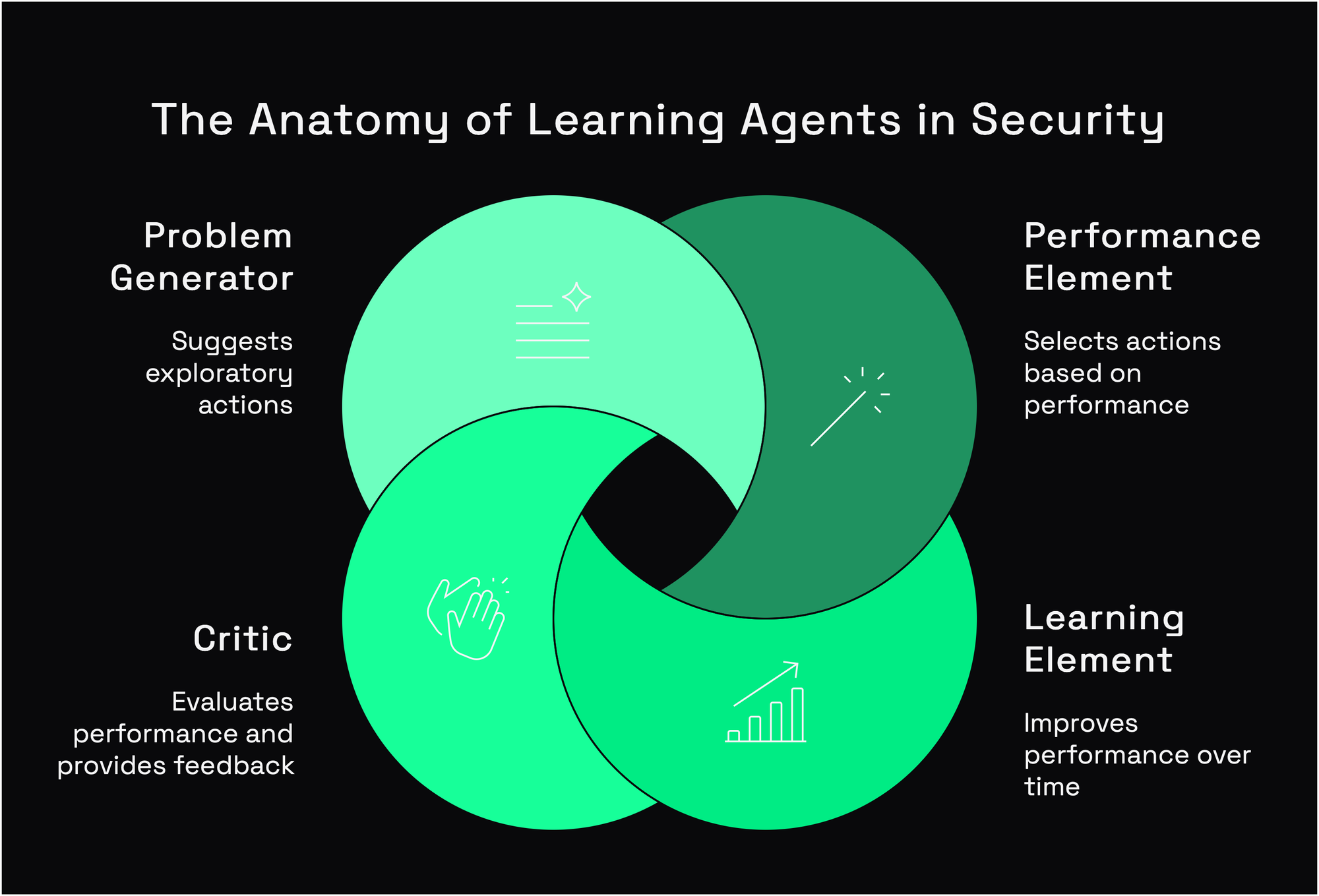
Learning agents are capable of combining aspects of all previous types while adding the crucial ability to improve through experience. Rather than relying on pre-programmed knowledge, these agents adjust their behavior based on feedback about their performance.
How They Work
The architecture of a learning agent typically includes:
- A performance element that selects external actions
- A learning element that makes improvements to the performance element
- A critic that evaluates performance and provides feedback
- A problem generator that suggests exploratory actionspseudocode
Learning agents have revolutionized security through:
- Advanced malware detection systems that continuously improve their recognition capabilities
- User and entity behavior analytics (UEBA) that learn normal patterns and detect anomalies
- Adaptive authentication systems that adjust security requirements based on risk signals
- Next-generation AV that identifies malicious behavior without relying solely on signatures
What makes learning agents invaluable for security:
- They can detect novel, previously unseen threats
- They reduce false positives over time by learning from mistakes
- They adapt to evolving attacker techniques without manual updates
- They personalize security responses to specific environments
A learning-based endpoint protection platform begins with some knowledge of malicious behavior but refines its understanding. When it flags a custom internal application as malicious, security analysts provide feedback.
The system learns from this correction, adjusting its model to recognize similar legitimate applications in the future. Simultaneously, when it blocks a new ransomware variant, this success reinforces its detection patterns.
Over time, the system becomes increasingly accurate at distinguishing between benign and malicious activity specific to the organization's environment.
The Security Implications of Agent Architecture
Understanding these five agent types can help you ask better questions to your vendors and select better products.
Furthermore, if you are planning on developing in-house AI agents (which I highly recommend), this can help you design and put in place the right agent for your use case.
| Agent Type | Security Strength | Security Weakness |
|---|---|---|
| Simple Reflex | Fast response to known threats | Blindness to novel attacks |
| Model-Based | Context awareness reduces false positives | Limited by quality of world model |
| Goal-Based | Proactive security planning | May pursue security at expense of usability |
| Utility-Based | Balanced security decisions | Complex to configure correctly |
| Learning | Adaptation to new threats | Potential for manipulation during learning phase |
When evaluating or designing security solutions, consider:
- Environment observability: How complete is your visibility? Simple reflex agents need full observability; model-based agents can work with partial information.
- Threat landscape: Are you primarily defending against known threats (reflex agents may suffice) or novel attacks (learning agents necessary)?
- Decision complexity: Do you need nuanced decisions that balance multiple factors? Utility-based agents excel here.
- Adaptation requirements: How frequently does your environment change? Learning agents provide the greatest adaptability.
- Explainability needs: Simple reflex and goal-based agents often provide clearer reasoning for their actions than complex learning systems.
The Future is Hybrid
While I've presented these agent types as distinct categories, modern security systems increasingly implement hybrid approaches. Today's most advanced security platforms combine:
- Simple reflex components for immediate response to known threats
- Model-based reasoning for context awareness
- Goal-based planning for proactive security
- Utility functions for balanced decision-making
- Learning capabilities for continuous improvement
What type of AI agent powers your security infrastructure? Are you leveraging the right architecture for your threat model? These questions are becoming increasingly central to effective cybersecurity strategy in our AI-driven world.
Before you go
If you found this post useful, I'd really appreciate if you could forward it to your community.
For more frequent cybersecurity leadership insights and tips, follow me on LinkedIn, BlueSky and Mastodon.
Best,
Nikoloz