Principled Pragmatism: How to Balance Security Ideals With Legacy System Realities

Nikoloz Kokhreidze
Stop choosing between ideal security and operational constraints. Learn how to implement a staged security roadmap that bridges the gap between legacy systems and modern protection standards.

You're standing at a crossroads. In one hand, you hold the blueprint for your perfect security architecture – modern, robust, and aligned with every industry best practice. In the other, you clutch a stack of reports about legacy systems that power critical business functions but haven't seen updates since Obama's first term.
Sound familiar?
If you're a security leader caught between idealism and operational constraints, you're not alone. I've spent over a decade navigating this exact tension. The question that haunts many of us remains: Should we aim for security perfection and make exceptions when needed, or should we build our security approach around existing business constraints from the start?
Your answer to this dilemma shapes your entire security program, team culture, and the value you deliver to your organization.
The Idealist's Trap (And Why I Fell Into It)

Early in my career, I was the definition of a security purist. I'd walk into meetings with vendors and business stakeholders armed with a comprehensive security wish list. "We need zero trust architecture," I'd declare. "We need to segment all networks, implement strong encryption everywhere, and replace anything older than three years."
People would nod, seeming to agree. Then came implementation time.
"That legacy ERP system? It can't support modern authentication protocols."
"That specialized manufacturing software? The vendor went out of business in 2014."
"That custom-built application? The developer who built it retired years ago."
My perfect security vision crashed against the rocks of operational reality. Business units pushed back. Relationships grew tense. Eventually, I realized my approach was fundamentally flawed.
I was building security castles in the sky without understanding the ground beneath them.
The Operational Realist (And Why That's Not Enough Either)
Some security leaders take the opposite approach. They begin with business needs and build security measures around existing constraints. This approach has merits – it acknowledges reality, minimizes business disruption, and often faces less resistance.
But it comes with serious downsides.
When you start by accepting all operational limitations as fixed, you often end up with inadequate security. You stop pushing for necessary changes. You stop challenging the status quo. And most dangerously, you become the department of "no, we can't secure that properly" rather than "yes, and here's how."
As Michael Oberlaender notes, security needs to "blend into the overall business processes and operational efficiency – so, instead of becoming a roadblock in every single undertaking, ensure that security is becoming part of the process." But that doesn't mean accepting every limitation.
Is security blocking your next enterprise deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
The Third Way: Principled Pragmatism
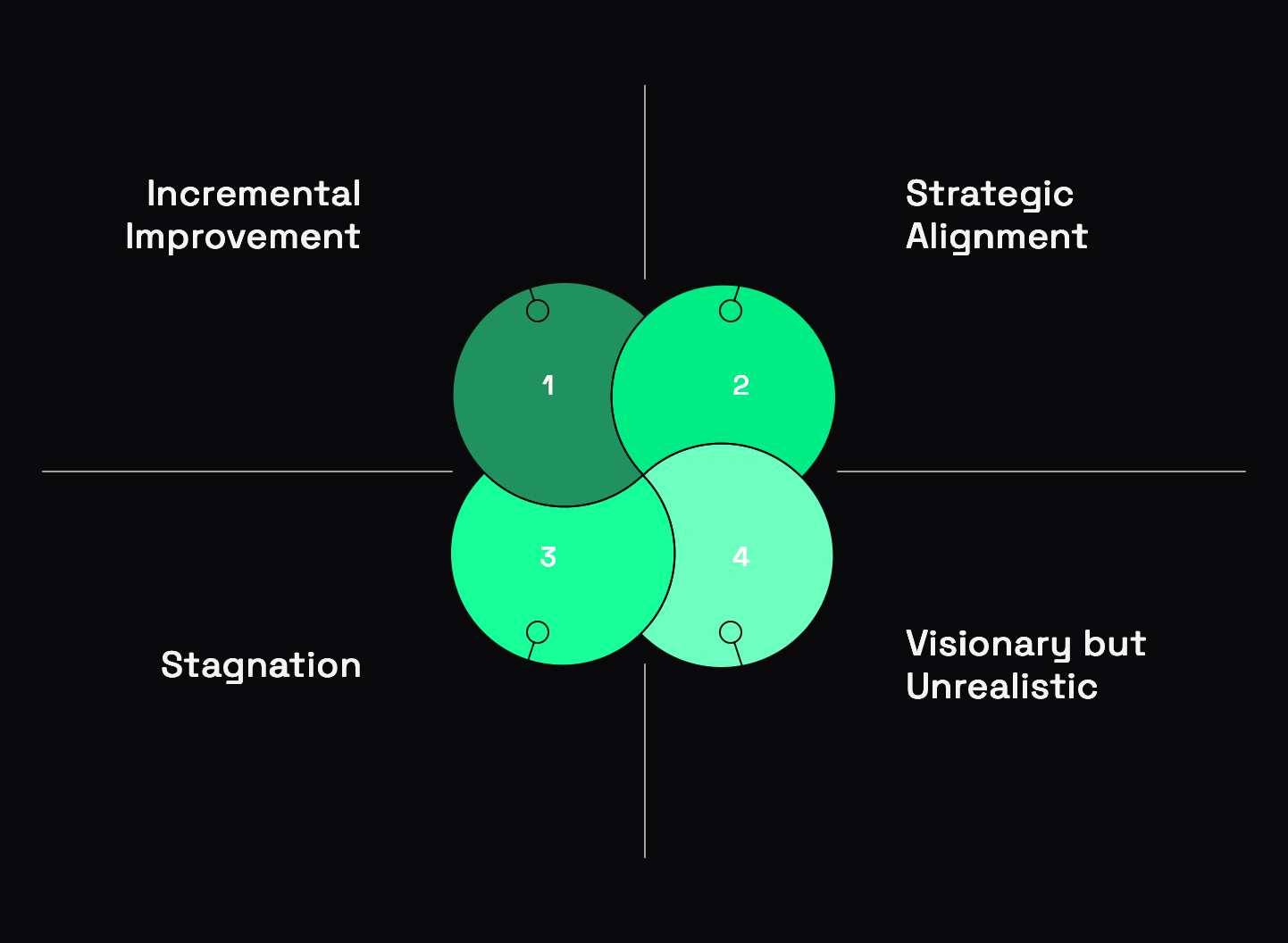
After years of wrestling with this dilemma, I've discovered there's a third path. I call it Principled Pragmatism. It combines the best of both approaches while avoiding their pitfalls.
Here's how it works:
- Start with your ideal security vision – be ambitious and forward-thinking
- Map this vision against your current operational reality
- Create a staged roadmap to bridge the gap
- Partner with the business to move forward together
Securing Legacy Systems Without Losing Your Mind
Legacy systems aren't going anywhere. According to research from Carnegie Mellon University, "Legacy systems continue to play a key role across many organizations. Engineering cybersecurity into these legacy systems presents some unique challenges."
But "challenging" doesn't mean "impossible." Here's my practical framework for securing legacy systems without compromising your security principles:
1. Segment and Contain
First, contain the risk. Legacy systems should operate in isolated network segments with strict access controls. By implementing microsegmentation, you limit the potential damage if these systems are compromised.
I once worked with a manufacturing company running critical machines on Windows XP long after support ended. Rather than fighting a losing battle to upgrade immediately, we isolated those systems on separate VLANs, implemented application whitelisting, and controlled all connections in and out. This bought us time to plan a proper upgrade path.
2. Compensate Where You Can't Eliminate
For every security gap in a legacy system, implement compensating controls around it.
If your legacy system can't support modern authentication, implement strict network access controls, enhanced logging, and behavioral monitoring. If it can't be patched, use application firewalls and regular vulnerability scanning.
The key is to be honest about the gaps while creative about addressing them.
3. Document Your Exceptions (And Their Expiration Dates)
Every security exception should be documented with three critical elements:
- The specific security requirement being excepted
- The business justification for the exception
- An expiration date or trigger for review
This creates accountability and prevents "temporary" exceptions from becoming permanent security gaps. It also forces honest conversations about when legacy systems need to be replaced.
4. Build Modernization Into Your Security Roadmap
Security isn't just about protection – it's about enabling safe business operations. That means your security strategy must include plans for modernization.
According to one industry study on system modernization, "Many legacy systems were likely built with limited or no concern for cybersecurity. Software engineering processes for cybersecurity change often." Your job is to help the business understand when modernization becomes a security imperative, not just a nice-to-have.
Security Architecture: Top-Down or Bottom-Up?
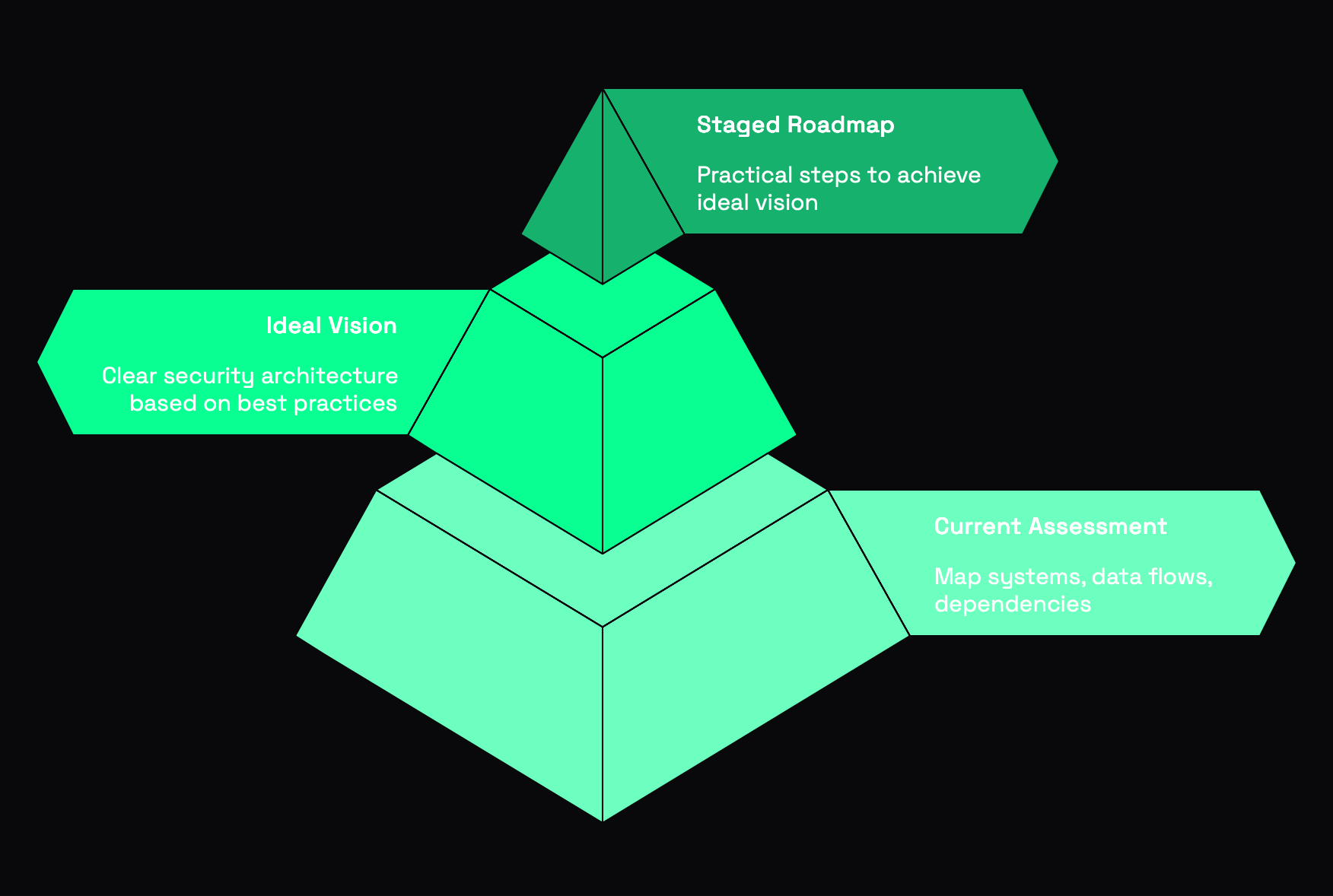
Now let's return to our original question. Should we start from the ideal and work backwards, or build from the current reality upwards?
After years in the trenches, my answer is: both, but in the right sequence.
Start with your north star – a clear, ideal security architecture based on current best practices and a deep understanding of your organization's risk profile. This gives you direction and purpose.
Then, conduct a clear-eyed assessment of where you are today. Map all systems, data flows, and dependencies. Identify the gaps between current and ideal states.
Finally – and this is the critical part – create a staged roadmap that moves you from current reality to your ideal vision through practical, achievable steps.
This isn't compromising your security principles. It's applying them intelligently within the constraints of business reality.
The Practical Middle Path: A Case Study
Let me share a real example from my own experience that illustrates this approach.
I joined a firm that had grown through acquisitions, resulting in four different identity systems. None of them talked to each other. User provisioning was manual. Deprovisioning was inconsistent.
It was a disaster waiting to happen.
The ideal solution was clear: a unified identity platform with centralized governance, automated provisioning/deprovisioning, and strong authentication. But simply declaring "we need to rebuild everything" would have been rejected immediately.
Instead, we took a strategic approach:
- We created our ideal reference architecture for identity
- We mapped all existing systems and identified the highest risk gaps
- We implemented a unified governance layer that sat on top of existing systems first
- We prioritized connecting the most critical applications to this governance layer
- We created a three-year roadmap to gradually replace legacy identity systems
With each phase, we reduced risk while moving toward our ideal architecture. Business leaders supported the approach because it delivered incremental value without disrupting operations.
When to Push Back on Operational Constraints
I use a simple framework:
- High risk, high business value: Partner on risk reduction. When critical business systems have security flaws, work closely with business leaders on compensating controls while developing upgrade paths.
- High risk, low business value: Challenge these constraints aggressively. If a legacy system creates significant security risk but delivers minimal business value, push hard for replacement.
- Low risk, any business value: Focus elsewhere. Not every legacy system needs immediate attention. Prioritize your efforts where risks are highest.
The McCary Group points out that strategic modernization requires understanding that "legacy systems have historically served as the backbone of many organizations, yet they now present significant challenges." The key is to identify which challenges represent genuine security risks.
Building A Culture of Security Pragmatism
For this approach to succeed, you need more than just a strategy – you need a culture of security pragmatism throughout your team.
This starts with how you hire. Look for security professionals who understand both technical security and business realities. Value those who can translate complex security concepts into business terms.
Next, set clear expectations. Make it clear that "perfect" security isn't the goal – effective risk management is. Recognize team members who find creative solutions to secure legacy systems, not just those who identify problems.
Finally, invest in relationship building. Security teams that have strong relationships with IT operations and business units can accomplish far more than those who remain isolated.
The Bottom Line
The tension between security idealism and operational reality isn't going away. But you don't have to choose one over the other.
By setting a clear security vision, understanding your current reality, and building a pragmatic roadmap between them, you can deliver real security improvements without ignoring business constraints.
Remember that securing legacy systems isn't a temporary problem to solve – it's an ongoing challenge to manage. Every organization has legacy systems, and there will always be operational constraints on security. Your job isn't to eliminate these constraints, but to work effectively within and around them.
As security leaders, our ultimate measure isn't how perfect our security architecture looks on paper. It's how effectively we reduce risk while enabling the business to thrive.
So yes, be an idealist about where you want to go. But be a pragmatist about how you get there. Your perfect security architecture might take years to fully realize, but with the right approach, you can make meaningful progress every step of the way.
That's not just effective security leadership – it's how you deliver lasting value to your organization.



