CISO's Guide to Securing the AI Data Pipeline

Nikoloz Kokhreidze
CISOs face unprecedented challenges in securing AI data pipelines. Learn about the complexities, risks, and a three-step guide to fortify your AI security posture.

CISOs are no strangers to the pressure of staying ahead of evolving threats. We've seen buzzwords come and go, but generative AI feels different. It brings a fundamental shift in how businesses operate, and with it comes a whole new set of security challenges.
Unfortunately, securing AI data often feels like trying to hit a moving target in the dark. Many organizations struggle to establish robust security for their AI initiatives, leaving sensitive data and even the AI models themselves vulnerable to compromise.
Why is securing AI data so complex?
AI security is a relatively new domain, and we're all still learning. The technology itself is complex, and the attack surface is constantly expanding. Many organizations lack the in-house expertise to effectively identify and mitigate AI-specific threats.
Adding to this complexity is the issue of speed. The AI industry is improving rapidly, and new tools, techniques, and, yes, threats emerge almost daily. This rapid pace of change can make it difficult to establish and maintain a robust security posture.
In response to these challenges, many organizations turn to third-party AI services or pre-trained models. However, it's dangerous to assume that the security burden falls solely on the provider. While providers play a crucial role, organizations must also take responsibility for their AI security.
This shared responsibility is particularly crucial when it comes to data protection. After all, data is the king in AI. AI thrives on it, and often, that data is incredibly sensitive. Training data, user inputs, and even the AI model's outputs can contain confidential information that must be protected.
While securing data is essential, it's important to remember that technology alone cannot guarantee security. In fact, our employees are often the weakest link in any security chain. Lack of awareness, accidental data sharing, or even malicious insiders can undermine even the most robust security controls.
Despite these challenges in AI security, from rapid technological changes to data protection and human factors, there's reason for optimism. Just like with any cybersecurity challenge, securing your AI data pipeline is about taking a proactive, strategic, and optimistic approach.
Here's a three-step guide to help you get started:
Is Security Blocking Your Next Enterprise Deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
Step 1: Know Your Data, Your AI, and Your Risks
This step is all about gaining clarity and laying the groundwork for a targeted security strategy.
To achieve this clarity, begin by identifying all AI initiatives within your organization. This includes understanding the types of AI applications in use (e.g., chatbots, content generators, predictive models), the data they process, and where that data resides. By cataloging your AI landscape, you'll be better equipped to assess and address potential risks.
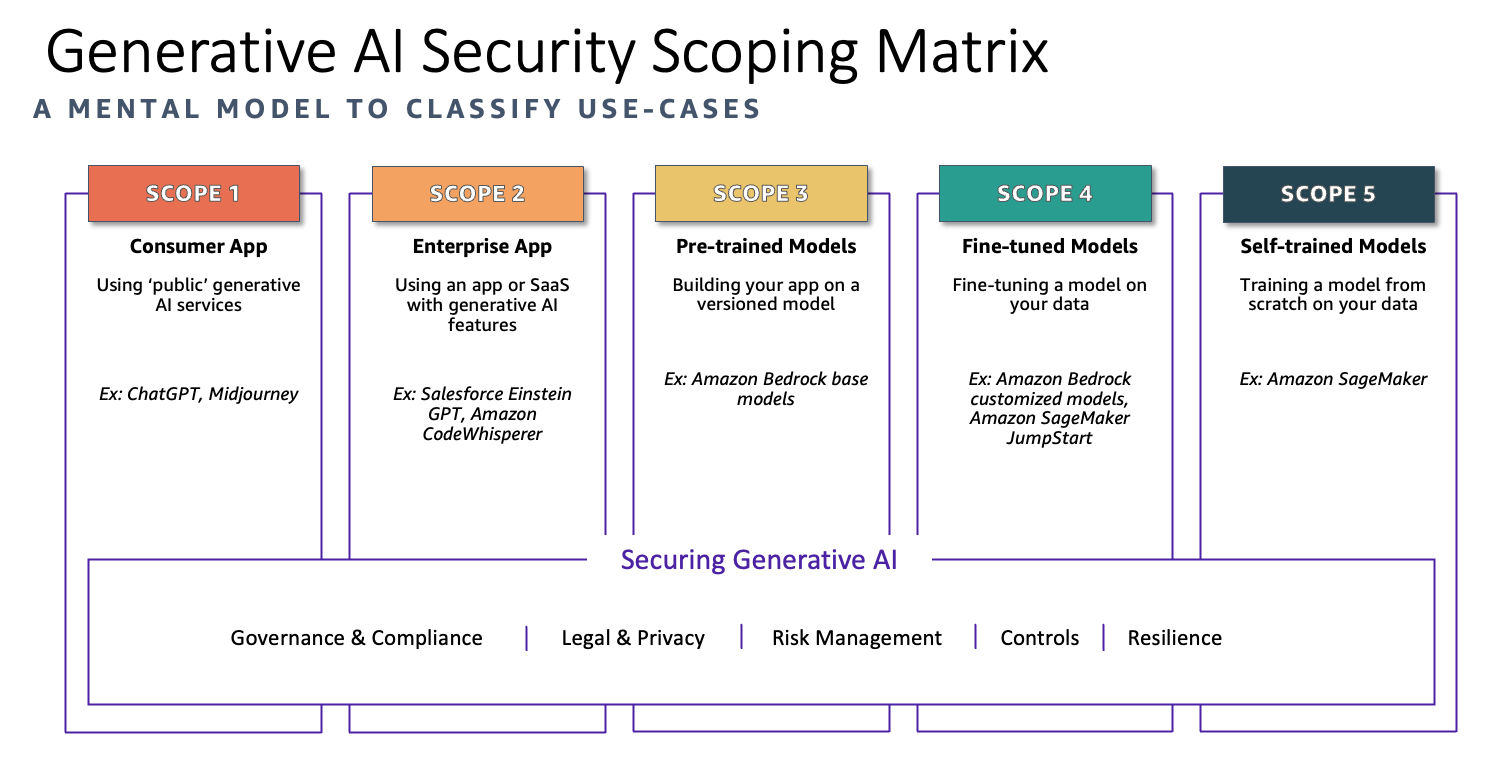
Once you've identified your AI initiatives, it's crucial to categorize them within a structured framework. AWS introduced a valuable tool for this purpose called the "Generative AI Security Scoping Matrix". This matrix categorizes AI usage into five distinct scopes, ranging from utilizing public AI services like ChatGPT (Scope 1) to building and training your own AI models from scratch (Scope 5). Each scope has its own risk profile and requires a tailored approach to security.
With your AI initiatives categorized, the next step is to visualize how data moves within your AI applications and across different systems. Building upon the scopes identified in the matrix, use data flow diagrams to illustrate these paths, highlighting potential points of vulnerability and where to focus your security controls.
Step 2: Build Your AI Security (Brick by Brick)
Now it's time to translate your understanding of risks into tangible security controls. The good news is that many well-established security principles still apply.
Just like with any critical system, you need to restrict access to your AI models, training data, and APIs. This means implementing strong authentication, authorization, and role-based access control (RBAC) mechanisms. The principle of least privilege is crucial here – only grant users the bare minimum access they need to perform their tasks.
In addition to access control, another crucial security measure is encryption. Encrypt your data at rest and in transit, including training data, model artifacts, and any sensitive information processed by your AI applications. Additionally, consider techniques like data minimization (only collecting and storing the data you absolutely need) and de-identification (removing or masking identifying information) to further reduce your risk surface.
While technical controls like access management and encryption are essential, it's equally important to approach AI security from a strategic perspective. This is where threat modeling comes into play. Traditional threat modeling needs an AI-specific makeover. This means understanding potential threats unique to AI systems, such as prompt injection, where attackers manipulate AI outputs by carefully crafting malicious inputs. Consider tools like Amazon Bedrock Guardrails, which allow you to define policies and filters to detect and mitigate undesirable content in both user inputs and AI outputs.
As part of your comprehensive AI security strategy, don't overlook the importance of evaluating your AI vendors' security practices. Through my experience and discussing with peers I have found that most business leaders assume that AI vendors have security all figured out. This is all very wrong. Carefully review their security policies and practices, and don't hesitate to ask tough questions. Thorough vendor assessment, combined with the internal security measures discussed earlier, will help ensure the overall security of your AI systems.
Is Security Blocking Your Next Enterprise Deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
Step 3: Empower Your People, Foster Collaboration, and Never Stop Learning
As much as we might want it, as long as humans are involved, technology alone can't secure your AI initiatives. You need to cultivate a security-first culture and empower your people to be your first line of defense.
Conduct regular training to educate your employees about AI-related security risks, data handling policies, and reporting procedures. The more they know, the better equipped they'll be to spot and report potential issues.
In addition to internal training, it's crucial to stay connected with industry peers and share information about emerging threats and best practices. We all know that the AI security world is constantly evolving, so keep connecting on professional platforms, attend conferences, and don't be shy to share your pain points. Trust me, your peers are in the same boat.
While staying informed about industry developments is important, it's equally critical to regularly monitor your own AI systems for suspicious activity. Analyze security logs, conduct penetration testing, and use the insights you gain to continuously improve your security posture.
Conclusion
By embracing these steps, you're not just securing your AI data pipeline – you're building trust with your customers, safeguarding your organization's reputation, and ultimately creating a more secure and resilient future.
A robust AI security program should result in reduced risk of data breaches, improved compliance with relevant regulations, increased user confidence in your AI initiatives, and a stronger overall security posture. The only constant is change, and the organizations that prioritize security will be the ones best positioned to thrive.
Before you go
If you found this article useful, I'd really appreciate if you could forward it to your community and share your feedback below!
For more frequent cybersecurity leadership insights and tips, follow me on LinkedIn, BlueSky and Mastodon.
Best,
Nikoloz
Grab your FREE checklist below.