Choosing a Security Operations Center: In-House, Hybrid, or Outsourced

Nikoloz Kokhreidze
Struggling to choose between an in-house, hybrid or outsourced Security Operations Center (SOC)? This guide helps you weigh pros, cons, costs, and business goals to make an informed decision.

Are you struggling to decide between an in-house Security Operations Center (SOC), hybrid, and outsourcing? This critical decision impacts your organization's cybersecurity posture and operations. In this guide, I will walk you through the steps to help you decide which option is the best for your use case.
What is the Security Operations Center (SOC)?
Before diving in, you should understand what a Security Operations Center (SOC) is. It is a centralized hub for an organization's cybersecurity needs, going beyond mere monitoring to provide a comprehensive suite of services. It continuously assesses the organization's networks, infrastructure, and endpoints for signs of security incidents, breaches, and vulnerabilities.
When a threat is detected, the SOC team uses incident response playbooks to contain and neutralize it swiftly to minimize risk. Automation tools are integrated to manage the volume of data and alerts, filter out false positives, and streamline processes. The SOC also engages in proactive threat hunting, sifting through networks and datasets to identify hidden threats that automated systems might overlook.
In addition to these operational tasks, the SOC plays a crucial role in ensuring compliance with industry regulations and standards. It generates detailed reports to both demonstrate compliance and inform senior management about the organization's holistic security posture.
Overall, the SOC is instrumental in strengthening an organization's cybersecurity defenses, minimizing risk, and enabling effective responses to security incidents.
Suppose SOC is something you are considering using. In that case, you will likely have to choose from three different types: in-house, hybrid, and outsourced.
Let's explore the pros and cons of each.
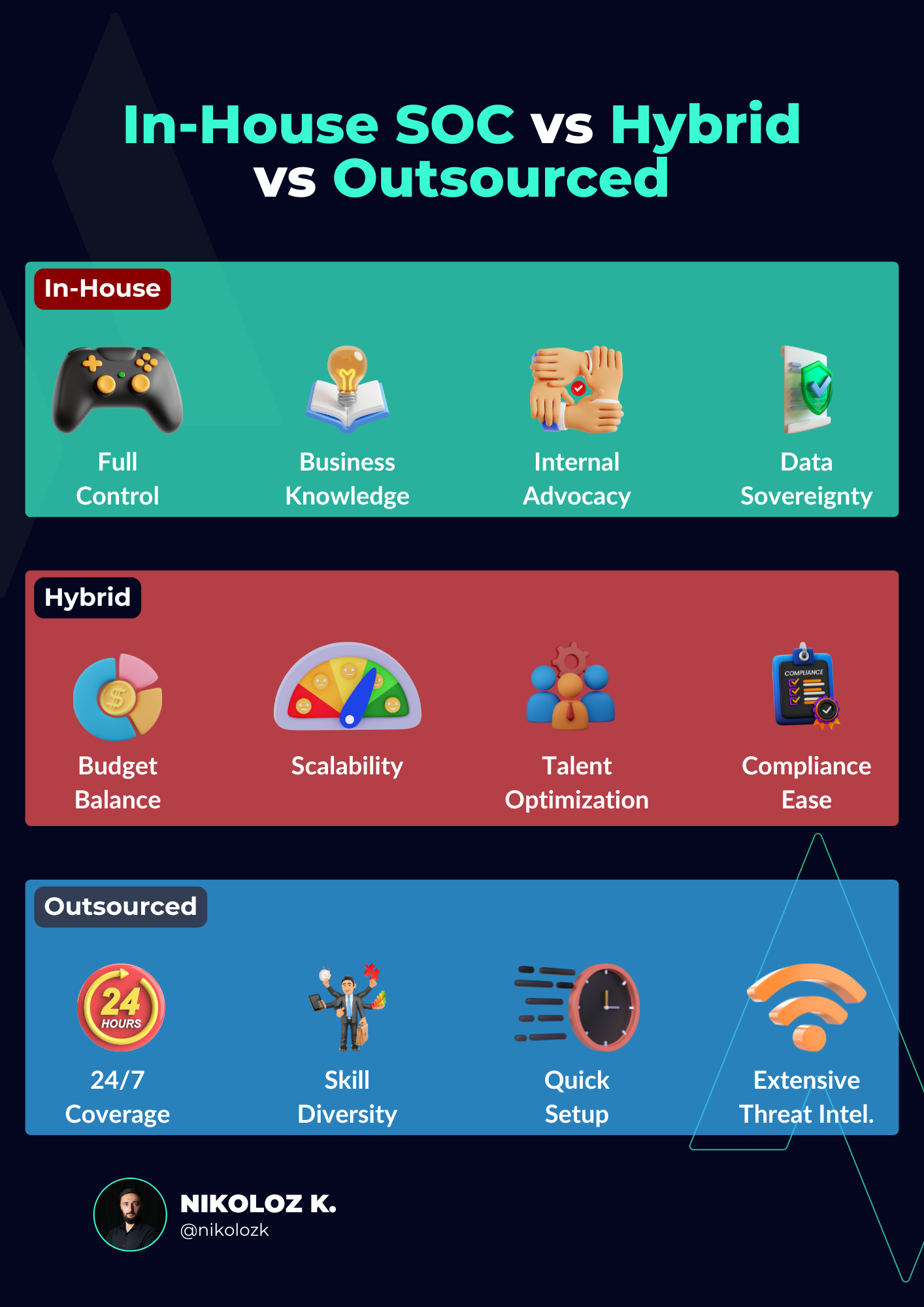
In-House SOC
| ✅ Pros | ❌ Cons |
|---|---|
| Tailor security protocols to fit your specific organizational needs. | Requires substantial investment in security tools and technology, which can quickly become outdated. |
| In-house teams can build a deep understanding of your unique infrastructure, leading to more effective security measures. | Smaller teams may face burnout due to the constant pressure and wide range of responsibilities. |
| An in-house team can be a strong internal advocate for security needs during budget and resource allocation discussions. | In-house teams might develop a narrow focus or blind spots, missing out on broader industry trends and threats. |
| Ensures that all data remains under local jurisdiction, which can be crucial for compliance. | Need of constant training and upskilling. |
Hybrid SOC
| ✅ Pros | ❌ Cons |
|---|---|
| You can balance the budget by keeping critical functions in-house and outsourcing less critical tasks. | Managing two different types of SOCs can be complex and may require specialized management skills. |
| Easier to scale your operations. You can add in-house resources or extend the outsourced contract as needed. | Effective communication between in-house and outsourced teams can be challenging. |
| You can allocate in-house staff to high-priority tasks while outsourcing routine monitoring, thus optimizing talent. | While it may seem cost-effective, managing multiple vendors and contracts can add hidden costs. |
| It is easier to meet compliance needs by keeping sensitive data in-house and outsourcing less sensitive tasks. | Data might be stored in multiple locations, making it harder to manage and secure. |
Outsourced SOC
| ✅ Pros | ❌ Cons |
|---|---|
| Most outsourced SOCs offer round-the-clock services, providing constant vigilance. | Service might be restricted by the terms of the contract, limiting flexibility in response to new threats. |
| Access to a broader range of skills and expertise that might be too expensive to maintain in-house. | The quality of service can vary significantly between vendors, and poor service can be detrimental. |
| It is faster to set up initially, as the outsourced SOC is already a functioning entity. | An outsourced SOC might not fully understand the specific business or industry culture, leading to gaps in service. |
| Benefit from a more extensive database of threat intelligence, often collected from multiple sectors and geographies. | Dependence on a particular vendor's tools and processes could make transitioning to another service or in-house operation costly and complex. |
Is Security Blocking Your Next Enterprise Deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
Making the Decision
Now, let's dive into the steps that will help you make the decision that is best suited for your organization, its objectives, and its culture. Keep in mind that not all steps might be necessary for your particular use case. My goal is to provide you with a holistic view of considerations that I had to take in while helping various organizations that have been at different stages of their security operations.
Step 1: Understand Your Business Needs
Before choosing between an in-house, hybrid, and outsourced Security Operations Center (SOC), it's vital to understand your business needs. Without aligning your information security and cybersecurity decision with your business goals, you risk creating a disconnect that could lead to inefficient resource allocation, increased vulnerability to threats, and, ultimately, a failure to meet key performance indicators or business objectives. The size of your enterprise, the industry you operate in, and your risk profile are key factors that will influence your decision.
Conduct a Risk Assessment
Start by understanding your environment, risks, and potential business impact.
- Identify Assets and Resources: List all the assets that need protection. This includes physical assets like servers and endpoints and digital assets like products, software, and cloud.
- Identify Threats and Vulnerabilities: Use tools like vulnerability scanners to find vulnerabilities and identify threats that can exploit those vulnerabilities.
- Assess Impact: For each vulnerability, assess the potential impact if exploited. Use metrics like financial loss or downtime.
- Prioritize Risks: Not all risks are equal. Rank them based on impact and likelihood.
- Consult Stakeholders: Involve key people like department heads, business leaders and IT managers in the risk assessment process.
Define Your Security Goals
Now that you are familiar with the environment and risks let's define the security goals that can help address those risks.
- Monitoring Needs: Decide what level of monitoring is needed based on the sensitivity of the data, risks associated with assets, business objectives, customer requirements, and internal processes.
- Compliance: Identify the legal and industry standards you must meet. This could be GDPR for data protection, HIPAA for health data or PCI DSS for payment security. Consider data masking.
- Response Time: Set a target for how quickly your team should respond to security incidents.
- User Training: Determine the extent of cybersecurity awareness training needed for your staff.
Step 2: Evaluate Costs
It would be best if you got a clear picture of the financial impact of both options. This isn't just about upfront costs, consider long-term expenses, too.
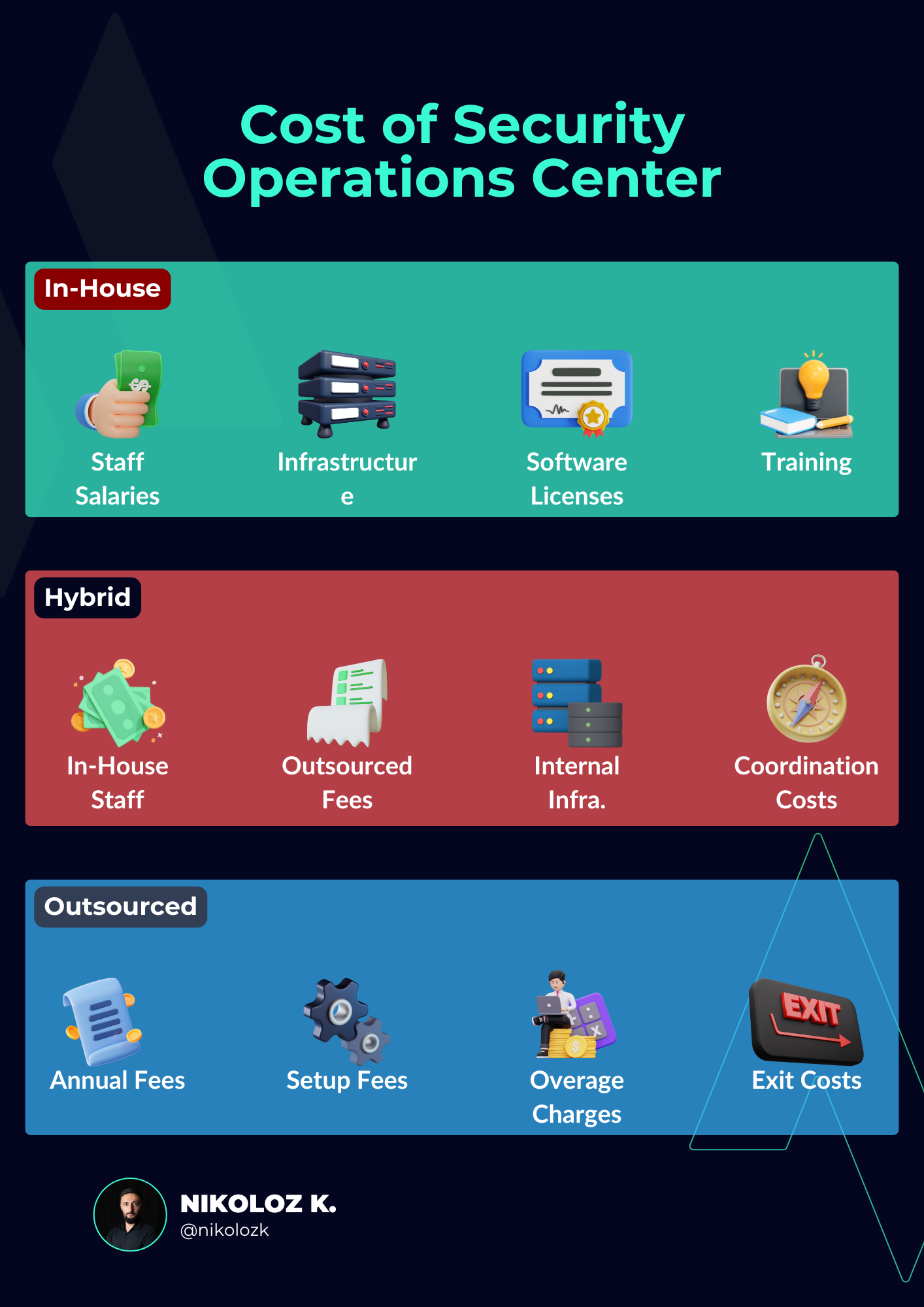
Identify Components of In-House SOC Costs
- Staff Salaries: Calculate the annual salaries for SOC analysts, engineers, managers, and other staff. Include promotions and salary raises.
- Infrastructure: Estimate the cost of computing, storage, detection and response infrastructure, licenses, other software and hardware.
- Software Licenses: Add up the costs of SIEM tools, EDR, ADR and other applications.
- Training: Factor in ongoing staff training.
- Utilities: Include electricity, internet, and other utilities.
- Sum Up: Add all these components to get the total annual cost of an in-house SOC.
Identify Components of Hybrid SOC Costs
- In-House Staff: Calculate partial salaries for roles you'll keep in-house.
- Outsourced Fees: Factor in monthly or annual fees for outsourced services.
- Infrastructure: You'll still need some in-house hardware.
- Software Licenses: Both in-house and outsourced services may require specific software.
- Coordination Costs: Time and resources spent on managing and coordinating between in-house and outsourced teams.
- Sum Up: Add all these to get the total annual cost of a Hybrid SOC.
Identify Components of Outsourced SOC Costs
- Monthly/Annual Fees: Get quotes from multiple vendors.
- Setup Fees: Some vendors charge an initial setup fee.
- Overage Charges: Understand what activities might incur extra costs.
- Exit Costs: Know the costs if you decide to terminate the service.
- Sum Up: Add all these to get the total annual cost of an outsourced SOC.
Evaluate
- Compare All Options: Create a side-by-side comparison chart for In-House, Outsourced, and Hybrid SOCs—factor in hidden costs like time spent managing teams or liaising with vendors.
- Consider ROI: Evaluate the return on investment for all three options. This could be in terms of reduced risk, faster response times, or other metrics significant to your business.
By doing this, you'll have a clearer financial picture to make an informed decision.
Is Security Blocking Your Next Enterprise Deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
Step 3: Assess Skill Requirements
To have a robust security posture, you need the right skills on your team. This step helps you identify those skills and see if your current team is up to the mark.
Here are the skills that I would recommend you to take into account.
In-House SOC
- Cyber Threat Analysis: Ability to identify and analyze potential threats specific to the organization's environment.
- Incident Response: Skills in managing and mitigating security incidents within the organization's network.
- Threat Hunting: Skills in proactively identifying unknown threats in the internal network before they cause harm.
- Network Security: Deep understanding of the organization's firewalls, intrusion detection systems, etc.
- Cloud Security: Expertise in managing the organization's cloud workloads, configurations, and deployments.
- Security Engineering: Skills in designing systems and integrations tailored to the organization's needs.
- Automation: Ability to automate repetitive security tasks within the internal environment.
- Scripting: Proficiency in scripting languages for custom security tasks.
- Windows Systems: Understanding of Windows-based security measures specific to the organization.
- Unix Systems: Knowledge of Unix/Linux-based security measures used in the organization.
- Stakeholder Communication: Skills in communicating incident details to internal stakeholders, aligning with corporate protocols.
- Compliance and Reporting: Proficiency in ensuring organizational activities meet established laws, regulations, and internal policies.
Outsourced SOC
- Vendor Oversight: Skills in managing and evaluating the performance and quality of outsourced services.
- Vendor Management: Ability to oversee and control interactions with third-party vendors.
- Contract Negotiation: Skills in securing favorable terms and minimizing risks in contracts with vendors.
- External Communication: Capability to interact effectively with external parties like vendors and regulatory bodies.
- Internal Incident Coordination: Ability to liaise between the outsourced SOC and internal departments, ensuring alignment with organizational policies.
- Compliance and Reporting: Proficiency in ensuring that outsourced activities comply with laws, regulations, and internal policies.
Hybrid SOC
- Internal-External Coordination: Ability to manage and coordinate between in-house and outsourced teams.
- Flexibility: Ability to adapt to changing security needs and configurations in both in-house and outsourced environments.
- Multi-Environment Management: Skills in managing security in both in-house and cloud-based environments.
- Data Segmentation: Understanding of what data to keep in-house and what to trust to an outsourced service.
- Incident Response: Skills in coordinating incident response activities between in-house and outsourced teams.
- Compliance and Reporting: Proficiency in ensuring that both in-house and outsourced activities comply with laws, regulations, and internal policies.
Analyze Skill Gaps and Coordinate
Now that you have the list of necessary skills. It's time to identify gaps.
- List Current Skills: Use a spreadsheet to list team members, stakeholders, and their skills.
- Compare with Core Competencies: Align this list with the core competencies needed.
- Evaluate the Cost of Skill Acquisition: Calculate the cost of training or hiring new staff with the required skills. Factor this into your overall budget assessment.
- Check for Internal Talent: Sometimes, employees from other departments have the skills you need. Consider internal transfers as a cost-effective way to fill skill gaps.
- Consult with HR: Work with your HR department to understand hiring timelines. This helps in planning if new hires are needed.
Step 4: Consider Scalability
Scalability is critical for long-term success, and this is where most SOC decisions fail. Often, organizations choose one of the categories of Security Operations Center that fits their current needs but do not consider the future growth of the company or long-term requirements. In my experience, this often leads to a situation where either:
- The internal team could not grow sufficiently quickly to catch up with business.
- Processes were not flexible enough to adapt the hybrid model with changes in internal operations.
- The security team ended up locked in with the service provider for a 3-5-year period and is not able to change contract terms to fit the new reality.
Your security setup should grow with your business. Here's how to assess scalability for both in-house and outsourced options.
In-House SOC Scalability
- Resource Flexibility: Assess the ability to quickly onboard new staff or scale down as needed.
- Tech Adaptability: Evaluate if your current technology stack can easily integrate new tools or scale existing ones.
- Process Evolution: Ensure that internal processes can adapt to increased workload or complexity.
- Budget Elasticity: Check if your budget can accommodate sudden scaling needs, both upwards and downwards.
Hybrid SOC Scalability
- Coordination Complexity: Evaluate how easily you can manage scaling across both in-house and outsourced components.
- Service Integration: Check if outsourced services can be easily integrated or removed without affecting in-house operations.
- Cost Predictability: Understand how scaling one component (in-house or outsourced) will impact overall costs.
- Flexibility in Transition: Assess the ease with which you can move from a hybrid to an entirely in-house or fully outsourced model if needed.
Outsourced SOC Scalability
- Contract Terms: Review the contract for clauses that allow for scaling the services.
- Vendor Capabilities: Assess if the vendor can handle increased workload or specific new requirements.
- Exit Strategy: Understand the costs and processes involved if you need to switch vendors for scalability reasons.
- Data Portability: Ensure you can quickly move your data if you decide to change vendors or bring services in-house.
By considering these factors, you'll be better equipped to choose a SOC model that not only meets your current needs but also scales effectively with your organization's growth and evolving security landscape. Given your extensive background in cybersecurity and strategic advising, this comprehensive approach to scalability will align well with both operational and strategic objectives.
Step 5: Examine Response Time
Response time is a vital metric in the effectiveness of a SOC. The speed at which SOC can detect, analyze, and respond to incidents directly impacts the severity and cost of a security breach.
Here's how to examine response time for In-House, Outsourced, and Hybrid SOCs.
Measure Your In-House Team's Response Time
- Define Metrics: Decide on key metrics like Time to Detect (TTD) and Time to Respond (TTR).
- TTD: The time it takes to detect a threat.
- TTR: The time it takes to contain and eliminate the threat.
- Run Simulations: Conduct mock cyber-attacks to test your team's response.
- Record Data: Log the TTD and TTR during these simulations.
- Calculate Average: Take the average TTD and TTR from multiple simulations for a balanced view - this will result in Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Evaluate the Outsourced/Hybrid Vendor's Response Time
- Request Metrics: Ask for the vendor's average MTTD and MTTR.
- Check SLAs: Review the Service Level Agreements (SLAs) for response times.
- Ask for Proof: Request case studies or performance data to validate their claims.
- Consult Reviews: Look for customer feedback on the vendor's response time.
Compare and Analyze
- Draw Comparisons: Put your in-house metrics side by side with the vendor's. Ensure that you can internally support in case of a major incident that requires shorter. response times
- Consider Variability: Understand that real-world scenarios can differ from simulations or promises.
- Make an Informed Decision: Choose the option that offers the best balance of speed and reliability and fits your organization's processes.
Step 6: Weigh Legal and Compliance Issues
Ensure that your security operations center, whether in-house, hybrid or outsourced, complies with all relevant laws, regulations, and industry standards. Take into account your industry and the one of your customers.
Identify Compliance Requirements
- List Applicable Laws and Regulations: Make a list of all laws and regulations that apply to your industry. This could include GDPR, CCPA, or HIPAA.
- Consult Legal Experts: Work with legal advisors to understand the implications of these laws on your SOC.
- Industry Standards: Identify any industry-specific standards like PCI DSS for payments or ISO 27001 for information security.
Assess Compliance Capabilities
- In-House Assessment: If considering an in-house SOC, evaluate your current infrastructure's ability to meet these laws and standards.
- Vendor Assessment: If considering outsourcing or hybrid, ask potential vendors for proof of compliance. This could be in the form of certifications or audit reports.
Gap Analysis
- Identify Gaps: Compare your current state with the required compliance levels. Note any gaps.
- Cost of Bridging Gaps: Calculate the cost and time needed to bridge these gaps for in-house, hybrid and outsourced options.
- Risk Assessment: Weigh the risks of non-compliance against the costs of achieving it.
- Final Review: Have a final consultation with your legal team to ensure all compliance issues are addressed.
Step 7: Make the Decision
Congrats, you have arrived at your final destination. At this stage the goal is to make a well-informed decision that aligns with your enterprise's needs, budget, and long-term goals.
Finalize Output from Previous Steps
- Compile Data: Gather all the data and insights you've collected from Steps 1-6.
- Create a Decision Matrix: Use a decision matrix to objectively compare the pros and cons of both options and which parts matter to you the most.
- Consult Stakeholders: Share your findings with key stakeholders for input.
Evaluate Risks and Benefits
- Risk Assessment: Revisit the risk profile of your organization. Does one option mitigate these risks better?
- Benefit Analysis: List the benefits each option offers. Consider factors like cost savings, expertise, and focus on core business.
Financial Considerations
- Budget Alignment: Ensure the choice aligns with your budget constraints.
- ROI Calculation: Estimate the return on investment for both options over a set period.
Make the Final Choice
- Review Compiled Data: Go through the decision matrix, stakeholder input, and your own analyses one last time.
- Make the Decision: Choose the option that scores highest in the decision matrix and aligns best with stakeholder input and your analyses.
- Document the Decision: Record why this choice was made for future reference and compliance needs.
By following these actionable steps, you'll be well-equipped to make a decision that not only addresses immediate security needs but also aligns with your enterprise's long-term objectives.
Conclusion
You've now learned a comprehensive approach to evaluate whether an in-house or outsourced Security Operations Center is the right fit for your enterprise. Your next steps could include implementing the chosen solution and continuously monitoring its effectiveness. If you found this guide helpful and need more insights, feel free to reach out for a tailored advise.
Is Security Blocking Your Next Enterprise Deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.



