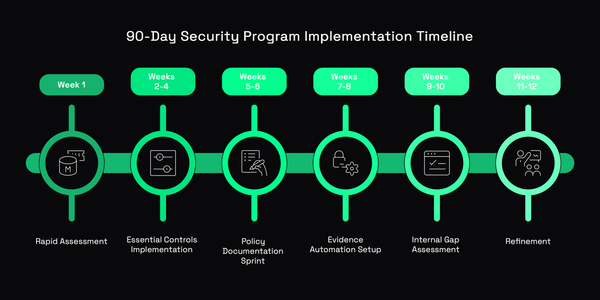
How to Develop Vision for a Successful Security Program

Nikoloz Kokhreidze
Learn how to create a security program vision that aligns with business. Use stakeholder identification and effective communication to secure leadership buy-in.

Security leaders must develop a clear vision for their security program to manage risks effectively. However, creating a vision is just the first step. To truly succeed, it is crucial to identify stakeholders, communicate the vision, ensure alignment with business goals, and secure buy-in from senior leadership and the board. In this article, we'll explore these crucial steps together to help you create a successful security program vision.
Step 1: Identify Key Stakeholders
The first step in developing a security program vision is identifying key stakeholders. These stakeholders include individuals, departments, or teams responsible for implementing, supporting, or reviewing the security program. For example, the IT department, risk management, legal, compliance, human resources, and senior leadership. Involving these stakeholders in the vision creation process ensures that their needs and concerns are considered and the vision is comprehensive.
- Conduct Interviews and Surveys: Engage with the identified stakeholders to gather their input on the security program vision. Ask them about their concerns, priorities, and suggestions for how the security program can best support their department's objectives. Be sure to communicate the importance of their input and make it clear that their feedback is valued.
- Hold Focus Groups: Organize focus groups with the identified stakeholders to discuss the security program vision in more detail. This can be an opportunity to get more in-depth feedback and stakeholder input. Ensure that these focus groups are inclusive and encourage participation from all attendees.
- Collaborate on Vision Development: Work together with the identified stakeholders on developing the security program vision. This collaboration can be facilitated through workshops, meetings, or other brainstorming sessions. Encourage stakeholders to share their ideas and work together to develop a comprehensive and inclusive vision.
- Provide Regular Updates: Keep stakeholders informed about the progress through regular meetings, progress reports, or other communication methods. Be sure to keep them updated on any changes or updates and invite their feedback and input as needed.
Step 2: Communicate the Vision Clearly and Consistently
Effective communication is critical for successful implementation. Once the vision has been developed, it is essential to communicate it clearly and consistently to all employees. The communication should include the importance of the vision, what it means for each department or team, and how it will be implemented. By doing so, employees can understand the impact of the vision and their role in its implementation, which can help them become more invested in its success.
- Utilize Various Communication Channels: Use town hall meetings, emails, Slack messages, and polls to share information about the vision and its implementation plan, ensuring the message reaches all employees.
- Use Clear and Concise Language: Avoid technical jargon unfamiliar to non-technical employees. Instead, use clear and concise language that is easily understood by all. Using examples or case studies that illustrate the benefits and the implementation process may also be helpful.
- Maintain Consistency in Messaging: Ensure that all employees receive the same message and that communication is consistent across all channels. Inconsistencies in messaging can lead to confusion or misunderstanding among employees, which can undermine the success of the security program.
Is Security Blocking Your Next Enterprise Deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
Step 3: Align with Broader Business Goals
The security program should not be seen as a separate entity within the organization but as an integral part of its overall strategy. Alignment with broader business goals can help ensure that the security program is viewed as a business enabler rather than a hindrance and supports the organization's mission and values.
- Involve Senior Leadership: To align with broader business goals, it's crucial to involve senior leadership in the vision creation process. Senior leaders can provide valuable input and guidance on how the security program can support the organization's strategic objectives. By involving senior leadership, you can also ensure that the security program vision is aligned with the organization's overall direction and priorities.
- Articulate the Link between the Security Program and Business Goals: Clearly demonstrate how the security program vision supports the organization's strategic objectives. For example, suppose the organization aims to grow its Tier 1 customers. In that case, the security program vision should support this objective by ensuring that security measures at your organization meet the requirements of such customers.
Step 4: Secure Buy-In and Support from Senior Leadership and the Board
To ensure the success of the security program vision, it's vital to secure buy-in and support from senior leadership and the board. Without their support, allocating the necessary resources and budget to implement the vision effectively will be challenging. Here are some steps you can take to secure buy-in and support:
- Develop a Business Case: Demonstrate the value of the security program vision to senior leadership and the board by creating a detailed business case. The business case should clearly articulate the need for the security program and how it aligns with the organization's strategic objectives. It should also highlight the benefits of implementing the vision, such as improved risk management, increased resilience, and enhanced customer trust.
- Present the Vision Clearly: Use visual aids, such as infographics or slides, to help convey your message when presenting the security program vision to senior leadership and board members. Ensure that the presentation aligns with the organization's strategic objectives and highlights the benefits of the vision.
- Address Concerns: Be prepared to answer questions and provide evidence to support your arguments when addressing any concerns that senior leadership and the board may have about the security program vision, such as cost, impact on productivity, or potential risks.
- Involve Them in the Process: Seek input and feedback from senior leadership and the board throughout the vision creation process. Keep them informed of progress and involve them in critical decision-making moments.
- Follow-up and Measure Results: Once the security program vision has been implemented, provide updates on progress and results to senior leadership and the board. Use metrics to demonstrate the effectiveness of the vision and its impact on the organization.
Step 5: Regularly Review and Update the Vision
Keep up with ever-evolving security threats and risks by regularly reviewing and updating your security program vision. As new threats emerge or your organization's strategic objectives change, adjust your security program accordingly.
- Collaborative Review Process: Involve key stakeholders, including senior leadership, department heads, and security professionals, in an effective review and update process. This collaborative approach can help identify gaps or areas for improvement in the current vision while ensuring alignment with organizational needs and goals.
- Communicate Updates: After reviewing and updating the vision, communicate the changes to all employees so they understand any shifts in the program's goals and objectives.
Step 6: Develop a Roadmap and Track Progress
Creating a roadmap and tracking progress is critical for achieving your security program vision. A well-defined roadmap outlines the steps required to achieve the vision, including specific tasks, actions, timelines, and resources needed.
- Break Down the Vision: Divide the vision into smaller, more manageable tasks to make tracking progress easier and ensure that each step is completed on time and within budget.
- Monitor Effectiveness: Tracking progress allows you to evaluate the program's effectiveness, make necessary adjustments, and identify potential areas of improvement or optimization.
Conclusion
By identifying key stakeholders, communicating the vision consistently, ensuring alignment with broader business goals, securing buy-in from senior leadership and the board, regularly reviewing and updating the vision, and developing a roadmap for implementation, you can create a successful security program that supports organization’s strategic objectives while mitigating risks.