Why Building Is Back in Cybersecurity And What It Means For Your Career

Nikoloz Kokhreidze
Security teams have surrendered autonomy to vendors. AI is democratizing development across security teams. Learn how to rebuild your engineering capabilities without hiring an army of coders.

For the past decade, security teams have been outsourcing our ability to build anything meaningful. They've become glorified procurement specialists, not security engineers.
I've watched security teams transform from builders to buyers. From creators to consumers. From engineers to evaluators.
The typical security department today has a handful of analysts, a small army of GRC professionals, and maybe - if they're lucky - one or two actual engineers who can build something from scratch.
We've convinced ourselves this is progress. That buying off-the-shelf solutions from vendors is the "mature" approach. That building custom tools is somehow unprofessional or unsustainable.
But this shift has come at a devastating cost: we've surrendered our autonomy, creativity, and ultimately, our effectiveness.
In this article, I'll show security leaders why the pendulum is swinging back to building, how AI is democratizing development capabilities across security teams, and the specific steps you can take to rebuild your team's engineering muscle. You'll learn how to identify high-impact automation opportunities, develop a practical building strategy that doesn't require hiring an army of engineers, and prepare your team for a future where building is no longer optional.
How We Lost Our Building Muscle
The erosion of our building capabilities didn't happen overnight.
It started innocently enough with the cloud revolution. As infrastructure moved to AWS, Azure, and GCP, the complexity of security tooling increased exponentially. Suddenly, building and maintaining custom security tools required specialized knowledge that many teams simply didn't have.
Then came the SaaS explosion and the pitch was compelling: focus on your core business and let us handle the technical heavy lifting.
Security leaders, already struggling with talent shortages and mounting compliance requirements, embraced this model wholeheartedly. We traded building for buying, engineering for evaluating, and creation for consumption.
The results speak for themselves:
- Skyrocketing costs with diminishing returns
- Endless integration challenges and data silos
- Complete dependence on vendors for innovation
- Security teams drowning in vendor management
- Bloated security stacks with dozens of disconnected tools
I recently spoke with a CISO at a mid-sized fintech who confessed: "We have 43 security tools, but can't answer basic questions about our security posture. We're spending millions on vendors but can't automate a simple offboarding workflow."
This is the reality for most security teams today. We've become hostages to our vendors, waiting for them to build the features we need, integrate with the systems we use, and solve the problems we face.
Is security blocking your next enterprise deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
The AI Inflection Point
But something fundamental has changed. We're at an inflection point that will redefine what's possible for security teams.
AI - specifically generative AI with its ability to understand context, generate code, and interface with systems - is democratizing the ability to build.
It's a paradigm shift that will separate forward-thinking security teams from those stuck in the procurement trap.
Here's what's different now:
- Code generation has become accessible to non-engineers. Tools like GitHub Copilot, Cursor, and Claude can generate functional code from natural language descriptions. You no longer need a CS degree to create useful automation.
- AI agents and tool calling capabilities are enabling seamless integration between systems. What used to require complex API development can now be accomplished through "AI-powered orchestration".
- Low-code/no-code platforms have matured, allowing security professionals to build sophisticated workflows without writing traditional code.
- The economics have flipped. Building custom solutions is becoming cheaper than buying and integrating vendor products for many use cases.
Why Building Matters Now More Than Ever

You might be thinking: "So what? Why should I care about building when I can still buy?"
Here's why this shift matters for every security leader:
Speed and agility. When you can build, you can solve problems immediately instead of waiting for vendors. I've seen security teams reduce response times from weeks to minutes by building custom automation.
Cost efficiency. The build vs. buy equation has fundamentally changed. Custom solutions built with AI assistance often cost a fraction of vendor products while delivering exactly what you need.
Competitive advantage. Security teams that can build custom solutions gain a significant edge over those dependent on vendors. They can address unique threats and requirements that off-the-shelf products can't handle.
Talent retention. Engineers want to build things. Analysts want to solve problems. When your team can actually create solutions instead of just implementing vendor products, engagement and retention improve dramatically.
Vendor leverage. When vendors know you can build alternatives to their products, your negotiating position strengthens considerably.
The New Security Builder's Toolkit
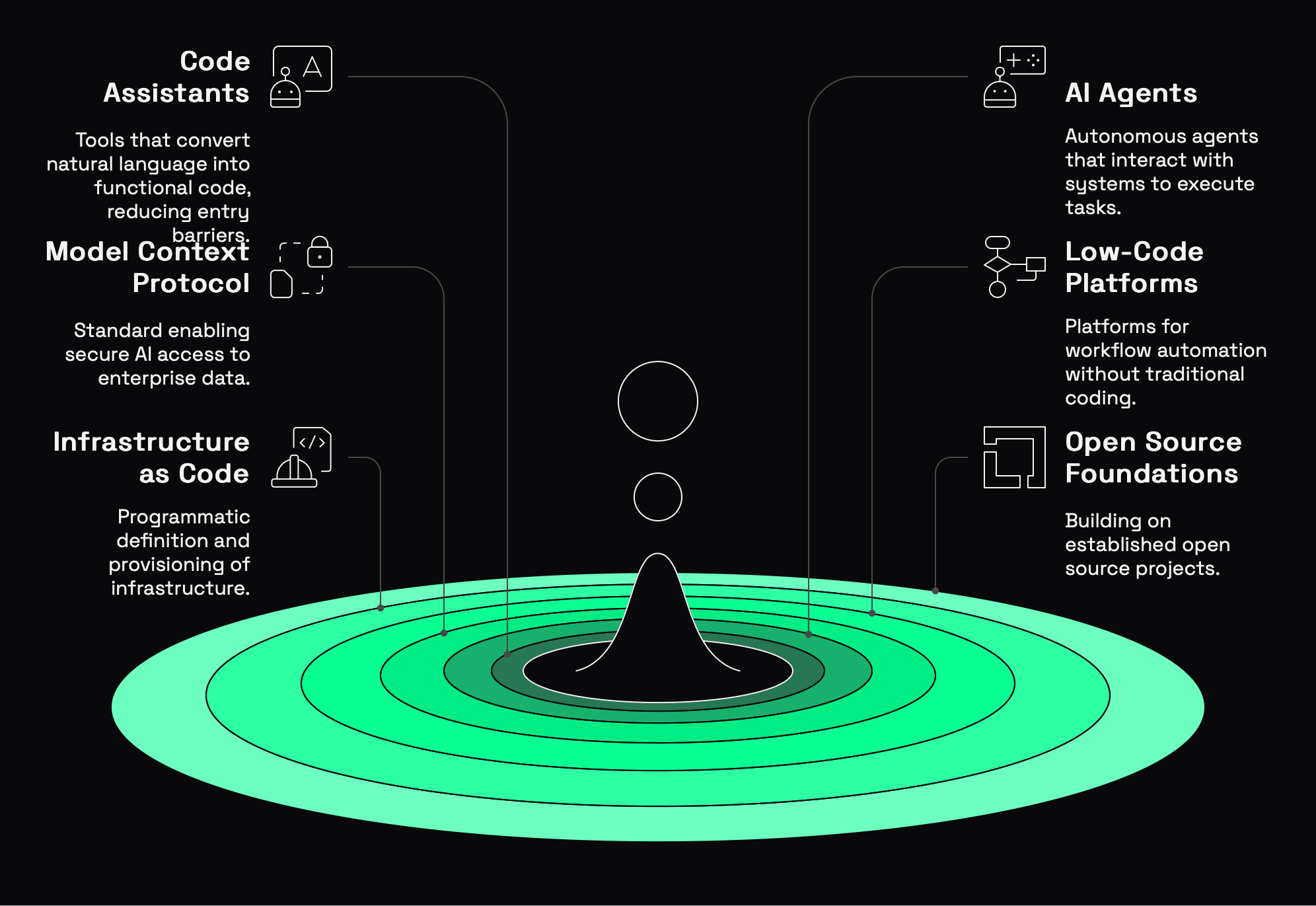
So what does this new building capability actually look like in practice?
It's not about hiring a team of full-stack developers or becoming a software company. It's about leveraging AI and modern tools to enable everyone on your security team to build solutions.
Here's what the modern security builder's toolkit includes:
AI Code Assistants: Tools like GitHub Copilot, Cursor and Claude can generate functional code from natural language descriptions. They're not perfect, but they dramatically reduce the barrier to entry for building.
AI Agents: Platforms like LangChain, AutoGPT, and Microsoft's Copilot Studio allow you to create autonomous agents that can interact with systems, retrieve information, and execute tasks.
Model Context Protocol (MCP): This emerging standard enables secure, controlled access to enterprise data for AI systems. It allows you to build tools that can safely reference your internal documentation, security policies, and proprietary data without compromising security.
Low-Code Platforms: Tools like Zapier, n8n, and Tines enable sophisticated workflow automation without traditional coding.
Infrastructure as Code: Terraform, CloudFormation, and Pulumi allow you to define and provision infrastructure programmatically.
Open Source Foundations: Build on top of established open source projects instead of starting from scratch.
The key point here is that these tools make building accessible to security professionals who don't have traditional software engineering backgrounds.
I've seen SOC analysts use these tools to automate alert triage processes. GRC professionals building custom compliance monitoring dashboards. Threat intelligence analysts creating specialized collection and analysis pipelines.
It's happening right now in forward-thinking security teams.
From Consumer to Creator: Practical Steps
So how do you transform your team from consumers to creators? From buyers to builders?
Here's a practical roadmap:
1. Start with high-impact, low-complexity automation
Begin by identifying manual, repetitive processes that cause friction in your security operations. These are perfect candidates for your first building projects.
Common examples include:
- Alert enrichment and contextualization
- User access reviews and certification
- Vulnerability management workflows
- Security questionnaire responses
- Compliance evidence collection
2. Upskill your existing team
You don't necessarily need to hire a team of engineers. Instead, identify people on your team who show curiosity and aptitude for building, regardless of their current role.
Provide them with:
- Access to AI coding assistants
- Time to experiment and learn
- Recognition for building useful tools
- Basic programming fundamentals training
3. Create a security automation platform
Establish a foundation that makes it easier for your team to build solutions:
- Document APIs and integration points
- Create reusable components and templates
- Establish coding standards and review processes
- Standardize on key technologies and frameworks
4. Adopt a product mindset
Treat your internal tools like products:
- Iterate based on feedback
- Measure impact and value
- Understand your users' needs
- Focus on usability and reliability
5. Balance building and buying strategically
Not everything should be built in-house. Develop clear criteria for when to build vs. buy:
- Build when you need custom functionality that vendors don't provide
- Build when integration between systems is critical
- Build when speed of implementation is essential
- Buy when specialized expertise is required
- Buy when the problem is well-defined and commoditized
Follow this approach and your team morale and retention will improve dramatically. People who were previously drowning in manual tasks will now be building solutions that will make their work more meaningful.
Is security blocking your next enterprise deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
The Future Security Leader Is a Builder
As we look to the future, one thing is clear: the most effective security leaders will be those who rebuild their teams' ability to create, not just consume.
This doesn't mean abandoning vendors entirely or becoming a software development shop. It means striking a new balance where building custom solutions is a core capability, not an exception.
The security leaders who thrive in this new era will:
- Foster a builder's mindset across their teams, encouraging everyone to look for automation opportunities
- Invest in AI-powered development tools that enable non-engineers to build effective solutions
- Create space for experimentation and learning, recognizing that building skills develop through practice
- Measure and celebrate the impact of internally built solutions
- Challenge vendors to provide more value or risk being replaced by custom alternatives
The days of the security leader as pure procurement specialist are ending. The future belongs to those who can build.
The Time to Rebuild Is Now
If you're reading this and thinking, "This sounds great, but my team doesn't have these skills," you're not alone. Most security teams have atrophied their building muscles over the past decade.
But here's the good news: rebuilding these capabilities is more accessible than ever thanks to AI and modern development tools.
Start small. Find one manual process that causes pain for your team. Challenge someone to build a solution using AI assistance. Celebrate the results. Repeat.
The transformation won't happen overnight, but it will happen—and faster than you might expect.
The alternative is to continue down the path of vendor dependence, watching your costs rise while your effectiveness plateaus.
The choice is yours. But remember: in a world where building is becoming democratized, those who can't build will ultimately fall behind.
Are you ready to rebuild?