Why Your Security Team is Wasting 70% of Their Time on Phantom Threats And How to Fix It

Nikoloz Kokhreidze
Your security team is spending 70% of their time chasing ghosts. Here's how to reclaim those hours for strategic work that actually matters.

Last Friday at 2:47 AM, your on-call security analyst was jolted awake by an urgent alert. The SIEM flagged suspicious authentication activity from an executive's account- potentially the early stages of a privileged access compromise.
After 90 minutes of painstaking investigation, correlating logs, checking endpoints, and running deep analysis on traffic patterns, the truth emerged: the executive was simply traveling internationally and logging in from a new location. Despite following proper protocols and using approved devices, the system triggered a high-priority incident.
This same story replayed across your security operations center 212 more times last month.
Sound familiar? You're not alone.
I've spent the past 13 years watching security teams trapped in this exhausting cycle. We've collectively built an incident response machine that's choking on its own alerts, draining the life from our teams, and undermining our strategic capabilities. And the worst part? We keep feeding this beast, thinking we're doing the right thing.
I'm here to tell you: we're deluding ourselves.
In this article you will get a no-nonsense approach to radically transform your incident response function to eliminate false positives, reclaim thousands of operational hours, and redirect your team toward strategic initiatives that genuinely improve your security posture.
At the end of the article Mandos Prime members will also get a step-by-step Notion blueprint to actually implement the changes and transform their IR processes.
The Brutal Reality of False Positives

According to recent cybersecurity research, a staggering 70% of SOC team time is spent investigating alerts that turn out to be false positives (source). That's not just inefficient - it's professionally negligent given today's threat landscape.
Is security blocking your next enterprise deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
The numbers get even more alarming:
- 33% of companies have been late responding to actual cyberattacks because they were tied up investigating false positives (source)
- 63% of cyber teams spend 4+ hours weekly dealing with false positives
- 15% spend more than 7 hours weekly on these phantom threats
While your analysts are busy investigating that executive's legitimate login from London, they're missing the actual ransomware dropper that just bypassed your perimeter controls.
But here's the most damning statistic of all: The vast majority of security teams know they have this problem, yet continue with the same broken approach, typically adding more tools and more alerts to the already overwhelming pile.
Why We're Stuck in This Loop
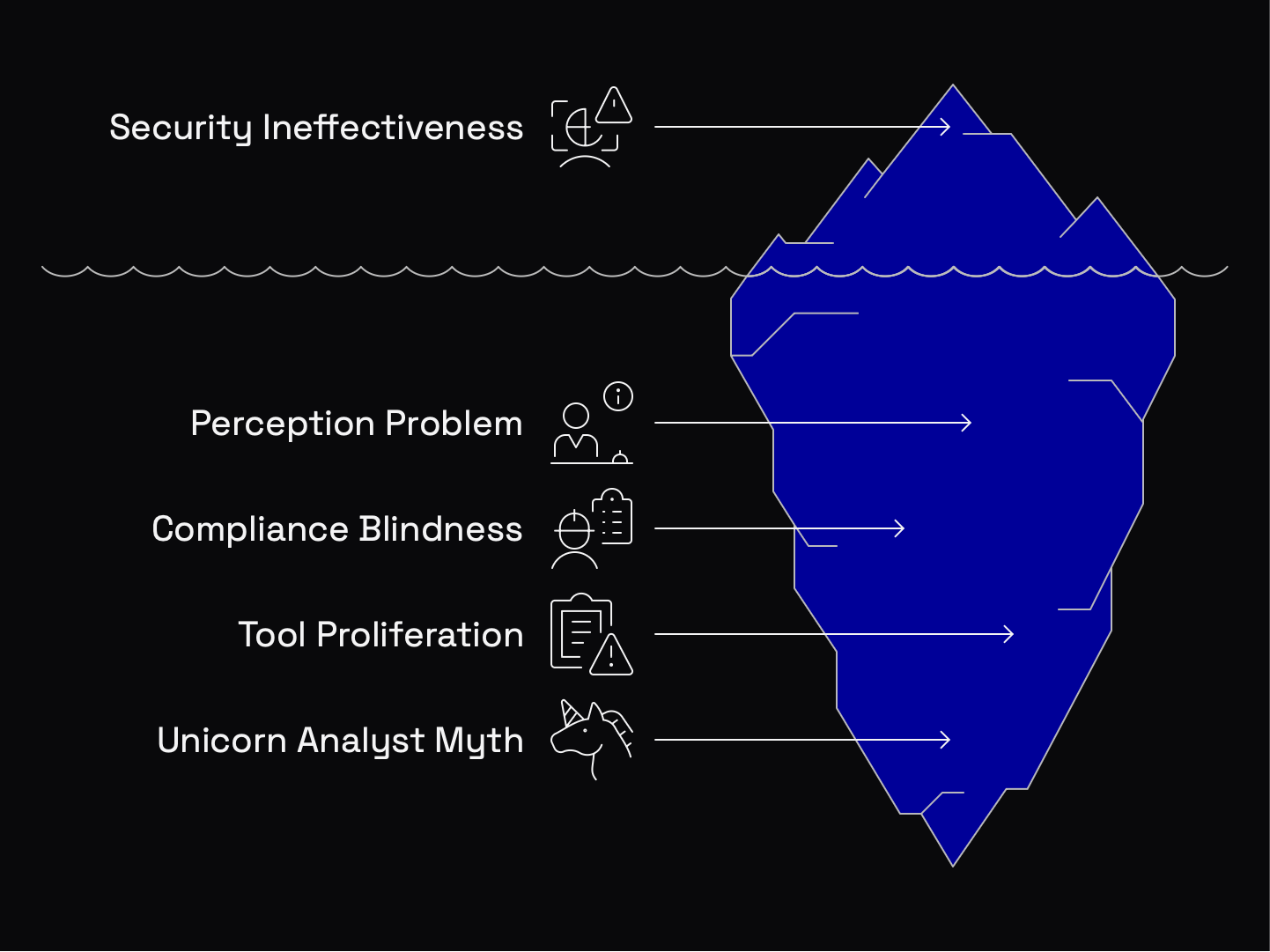
Let's examine why intelligent security leaders keep reinforcing this broken model:
- The Perception Problem: No CISO ever got fired for investigating too many incidents. But miss one real attack? Career suicide. This asymmetrical risk creates perverse incentives.
- Compliance Blindness: Many incident response programs are designed primarily to satisfy auditors rather than actually secure the business. We've prioritized documenting our response over making that response effective.
- Tool Proliferation Without Integration: The average enterprise now has 76 different security tools. Each one operates in isolation, generating its own alerts with its own limited context, overwhelming your analysts.
- The Myth of the "Unicorn Analyst": We've built programs assuming we'll find and retain security unicorns who can efficiently investigate anything from network anomalies to WAF exploits. These people don't exist in sufficient numbers.
- False Comfort from Activity: Security executives often confuse analyst busyness with effectiveness. "My team closed 300 incidents this month!" sounds impressive until you realize 90% were false alarms.
At one of my previous employers, I discovered their security team spent 14,400 analyst hours in a single quarter investigating what turned out to be benign activity. That's approximately seven full-time employees achieving literally nothing for an entire year.
The Real Cost Beyond Wasted Hours
The damage extends far beyond operational inefficiency:
Analyst Burnout and Attrition: Alert fatigue is driving our best people out of the field entirely. According to recent surveys, security professionals who moved from incident response to consulting reported substantially lower stress levels (source).
Decreased Vigilance: Psychologically, humans are terrible at sustaining attention when false positives are common. Your analysts become desensitized, inevitably missing critical alerts buried among the noise.
Opportunity Cost: Every hour spent on false positives is an hour not spent on proactive threat hunting, security architecture improvements, or strategic risk reduction.
As one CISO at a healthcare organization recently confided: "We've built an incredible machine for detecting minor problems while completely losing sight of what actually matters to the business."
Breaking Free: The Path Forward
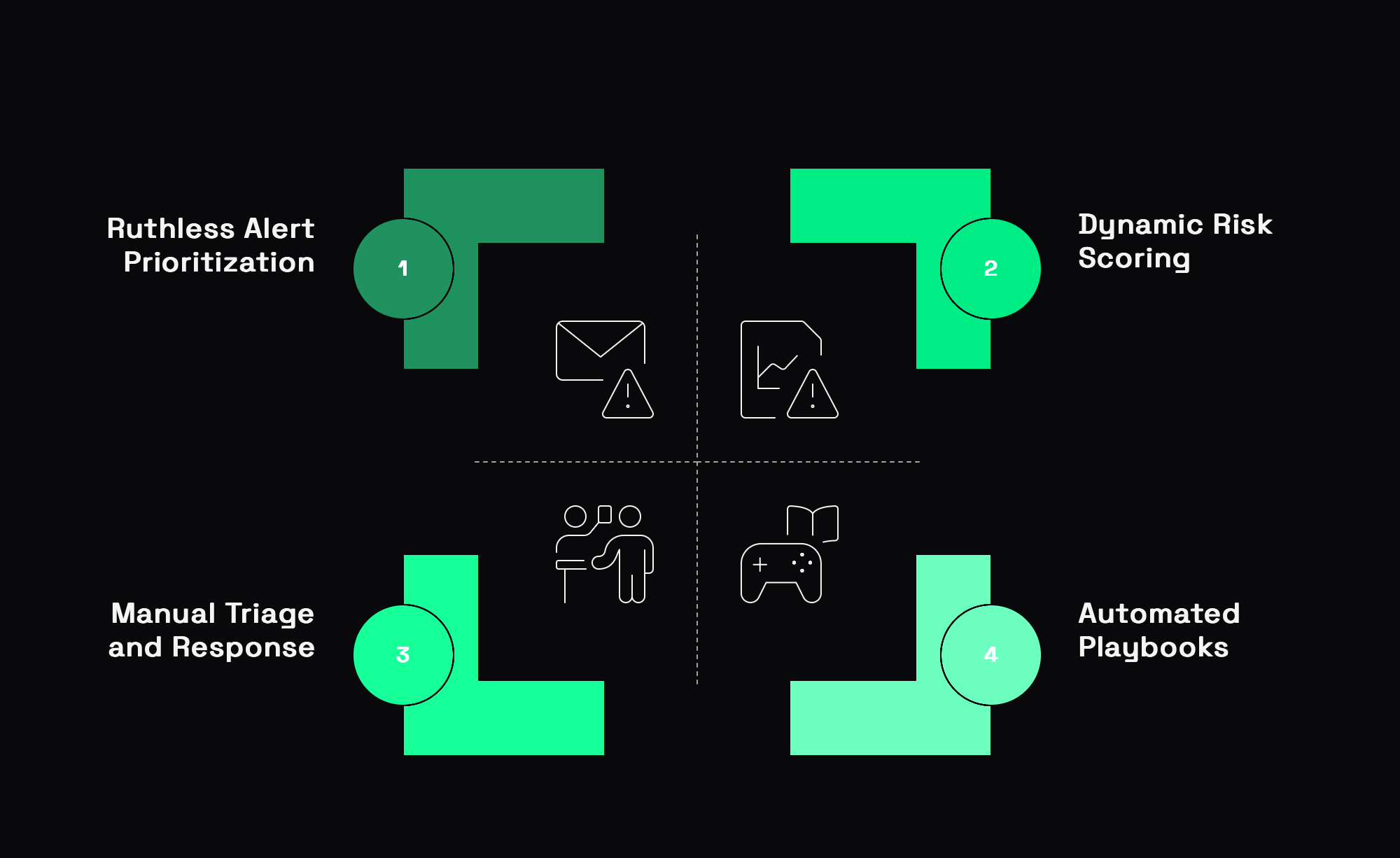
Enough doom and gloom. Let's talk solutions - not theoretical frameworks, but practical approaches I've implemented with real organizations that have transformed their incident response function.
1. Prioritize Ruthlessly with Context-Rich Alerts
The foundation of modern incident response must be ruthless prioritization based on actual risk, not just technical triggers. This means:
- Implement Risk-Based Alert Scoring: Every alert should carry a dynamic risk score based on the asset involved, user context, and potential impact - not just technical severity.
- Eliminate All Zero-Value Alerts: If an alert has consistently led to no action over time, it should be automatically disabled or severely demoted. Be brutal here.
- Enrich with Business Context: Security alerts without business context are nearly worthless. Integrate your CMDB, IAM systems, and asset management tools with your detection stack.
At a mid-sized financial institution, we reduced their daily alert volume from 3,600 to just 87 high-fidelity alerts by implementing dynamic risk scoring. The result? They caught more actual threats despite investigating 96% fewer alerts.
2. Embrace Automated Response (Not Just Detection)
Automation isn't just about detection - it's about response:
- Implement No-Human-Required Playbooks: For common, well-understood scenarios, build fully automated response workflows. No human should ever investigate a known-benign pattern.
- Use AI for Initial Triage: Modern AI-driven SOAR platforms can now perform initial investigation steps, gathering context and presenting analysts with summarized findings rather than raw alerts.
- Automate the Tedious Middle: The investigation steps between alert and resolution are often repetitive. Automate log collection, context gathering, and correlation.
Jonathan Fischbein, CISO at Check Point, implemented this approach and reported: "We can react automatically to problems before they become security incidents" while significantly reducing analyst fatigue (source).
Is security blocking your next enterprise deal?
Let's discuss how fractional CISO services can unlock your pipeline without the full-time overhead.
3. Redesign the Analyst Experience
Your analysts aren't alert-processing machines. They're skilled investigators being crushed under repetitive tasks:
- Implement a "No Alert Left Behind" Policy: Every single false positive should trigger an immediate tuning review. Make this a core metric.
- Create Feedback Loops: When analysts identify false positives, they should have direct channels to detection engineering to prevent recurrence.
- Rotate Responsibilities: Analysts stuck in alert triage for extended periods burn out. Create rotation programs that balance tactical and strategic work.
One organization I worked with reduced false positives by 83% in six months by implementing analyst feedback loops and making tuning a shared responsibility across security engineering and operations.
4. Leverage AI, But Get Specific
AI isn't a magic solution, but specific applications can transform incident response:
- Pattern Recognition: Use machine learning to identify patterns in historical false positives and automatically suppress similar future alerts.
- Natural Language Processing for Documentation: Deploy AI to automatically document investigations, freeing analysts from administrative burdens.
- Anomaly Contextualization: AI can rapidly correlate seemingly unrelated events that humans would take hours to piece together.
A recent implementation of AI-assisted analysis at a healthcare provider reduced investigation time for common scenarios by 62% while simultaneously increasing detection accuracy.
A Blueprint for Immediate Action
Here's your 30-day plan to begin the transformation:
- Perform Alert Triage Analysis: Document every alert source, volume, and false positive rate. Be ruthless about identifying low-value noise.
- Implement a False Positive Tracker: Create a simple system to log every false positive, its source, and the time spent investigating.
- Identify Your Top 5 "Time Sink" Scenarios: Which alert patterns consistently waste the most analyst time? These are your first automation targets.
- Set Up a Basic Automation Framework: Even simple scripting can eliminate repetitive investigation steps. Start with basic log correlation and context gathering.
- Establish Baseline Metrics: You can't improve what you don't measure. Track false positive rates, mean time to investigate, and analyst hours recovered.
When I implemented this approach at a global manufacturing firm, they recovered over 6,200 analyst hours in the first year - effectively adding three FTEs to their security team without hiring a single person.
Ready to implement the steps to transform your incident response?
Grab the blueprint and start building.
The Real Strategic Advantage
The ultimate goal isn't just operational efficiency. It's strategic realignment.
When your security team spends less time chasing ghosts, they can focus on truly strategic initiatives:
- Threat hunting to find what your tools missed
- Architectural improvements to eliminate entire classes of vulnerabilities
- Business enablement through security design patterns
- Strategic risk assessment and remediation
One CISO I worked with put it perfectly: "We used to measure success by how many incidents we handled. Now we measure it by how few incidents actually matter - and how quickly we resolve the ones that do."
The Bottom Line
The incident response delusion persists because we've accepted a broken status quo. We've convinced ourselves that drowning in alerts is just "how security works."
It doesn't have to be this way.
By implementing risk-based prioritization, embracing thoughtful automation, redesigning the analyst experience, and leveraging targeted AI solutions, you can transform your incident response function from a reactive alert factory into a strategic security capability.
The organizations that break free from the false positive trap don't just operate more efficiently - they fundamentally transform their security posture, moving from reactive firefighting to proactive risk management.
The question isn't whether you can afford to make these changes. It's whether you can afford not to.



