You Feel Like an Imposter and That's Okay: Here's How to Build Up Confidence

Nikoloz Kokhreidze
Cybersecurity imposter syndrome is practically universal among leaders. Learn how deliberate failure builds genuine confidence no certification provides.

Imposter syndrome isn't just common in cybersecurity leadership - it's practically universal. But here's what most people won't tell you: the leaders who appear most confident are usually the ones compensating hardest for their insecurities.
I've worked with hundreds of security leaders across multiple industries and geographies. The pattern is unmistakable. The louder they proclaim expertise, the more they're hiding their knowledge gaps.
The Uncomfortable Reality of Security Leadership
The root problem? Most security leaders don't have genuine confidence because they haven't faced enough failure. They've stayed comfortable in their specialties, avoided stretching into unfamiliar domains, and run from situations where they might look incompetent.
I see this constantly - CISOs who've never written a line of code making application security decisions. Security architects who've never responded to a real incident designing incident response programs. "Leaders" who delegate anything that might expose their knowledge gaps.
This isn't leadership. It's hiding.
In this article, I'll show you how deliberate failure builds genuine confidence, share my own humiliating security failures that ultimately created real expertise, and provide a practical Security Leadership Confidence Builder template for developing confidence that no certification can provide. You'll learn how to identify your own avoidance patterns and transform them into growth opportunities that build actual confidence in this field.
Why Most Security Leaders Stay Mediocre
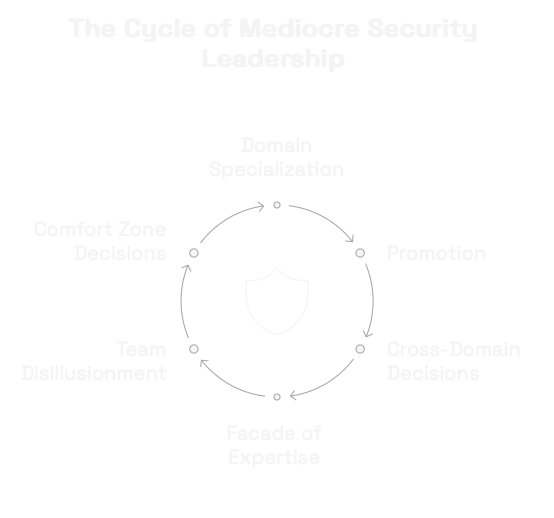
This is how most leaders progress in organizations:
- They specialize in one security domain (network security, AppSec, GRC, etc.)
- They get promoted to leadership position based on that expertise
- They suddenly need to make decisions across ALL security domains
- Rather than admit knowledge gaps, they fake expertise or delegate uncomfortable decisions
- Their teams see through the facade, but play along
This creates a dangerous cycle and leads to permanently feeling like an imposter. Why? Because the leader never develops true cross-domain understanding. Their teams don't respect their judgment. And the organization builds security capabilities based on the leader's comfort zone, not actual risk.
I've seen "cloud security experts" who couldn't explain basic container concepts. "Application security leaders" who've never written code. "Security architects" who draw impressive diagrams but can't explain how their controls would actually stop a sophisticated attack.
When pushed beyond buzzwords, they crumble. but not because they're incompetent (they are not) but because they've avoided the essential ingredient of mastery: deliberate failure.
My Most Humiliating Security Failures
When I first tackled cloud security in 2016, I failed spectacularly. I approached it like traditional infrastructure security and missed fundamental architectural differences. My designs were laughed out of the room by cloud engineers. I had two choices: retreat to my comfort zone and delegate "cloud stuff" to specialists, or push through the discomfort.
I chose discomfort.
I took AWS training that helped me better grasp the concepts. I spent six months building and breaking cloud environments in my spare time. I joined cloud engineering meetings and asked "stupid" questions that made me cringe. And most importantly I paired with engineers to understand how they interacted with cloud services.
After dozens of failures, patterns started emerging.
Concepts clicked.
I developed intuitions about cloud security that no certification could have provided.
Later, when building detection engineering capabilities, I faced similar humiliation. My first detection rules generated so many false positives they were immediately disabled. Again, I could have blamed the tools or delegated to "detection engineers." Instead, I immersed myself in log analysis, learned SIEM limitations firsthand, and iterated through failure after failure.
This process eventually led to me being hired by a leading Dutch Cyber Threat Intelligence company to build over 500 detection mechanisms across various operating systems and help design their XDR product.
The Confidence Paradox in Security Leadership
Here's the paradox most security leaders never grasp: real confidence doesn't come from appearing knowledgeable. It comes from being comfortable admitting what you don't know.
When you've survived enough failure, you develop a fundamental certainty: "I may not know this yet, but I can figure it out." This is genuine confidence - not in your existing knowledge, but in your ability to acquire new knowledge.
This transforms how you lead:
- You ask better questions instead of pretending to have answers
- You make more accurate risk assessments because you understand the limits of your knowledge
- You build more resilient teams because you model learning instead of posturing
- You make better technology decisions because you've experienced failure firsthand
Most importantly, you stop wasting energy maintaining a facade of omni-knowledge that everyone sees through anyway.
How to Deliberately Build Confidence Through Failure
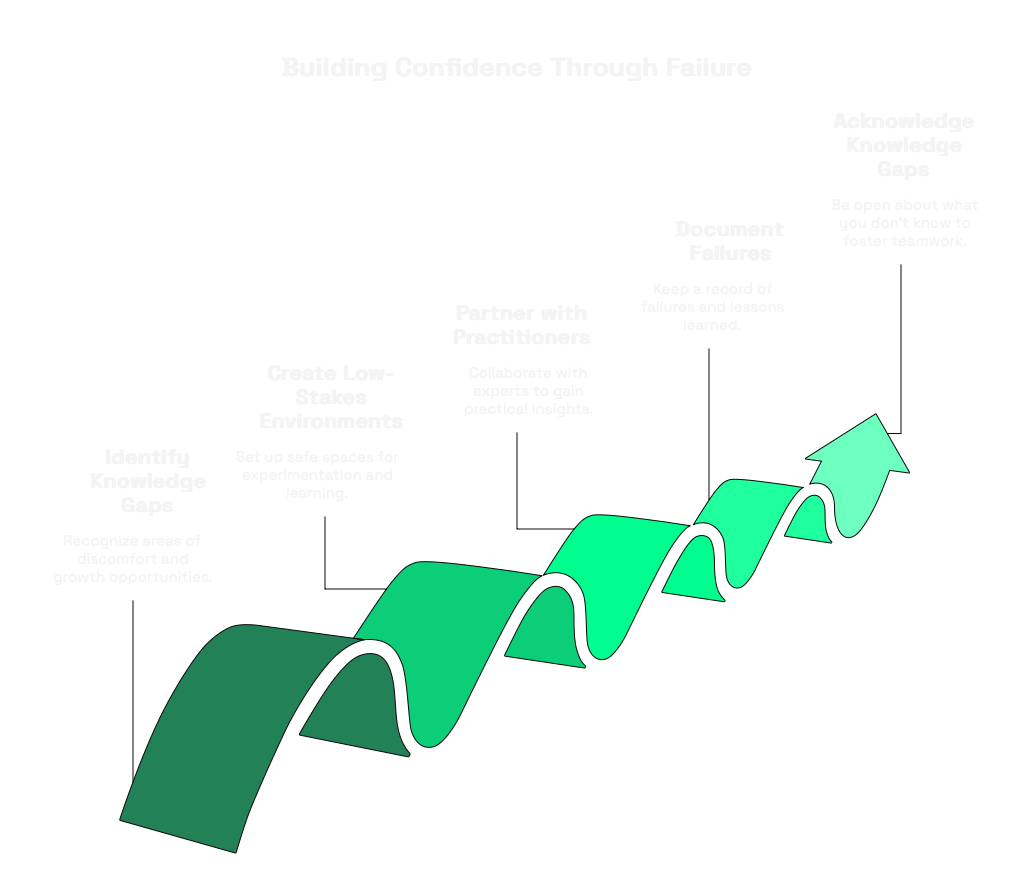
If you want to develop genuine security leadership confidence, you need to systematically expose yourself to failure. Here's how:
1. Identify your knowledge boundary zones
What security domains make you uncomfortable? Where do you delegate without understanding? What questions do you dread being asked? These are your growth opportunities.
When I realized I was avoiding cloud security conversations, I knew that's exactly where I needed to focus.
2. Create low-stakes failure environments
Set up personal labs, join open-source projects, or volunteer for cross-functional initiatives where you can fail without organizational impact.
I built dozens of cloud environments with the explicit goal of breaking them. Each failure taught me something certifications never could.
3. Partner with practitioners
Find engineers, developers or analysts who work daily in your discomfort zones. Shadow them. Ask stupid questions and let them see your learning process.
The cloud engineers who initially laughed at my designs eventually became my most valuable teachers when they saw I was genuinely committed to learning.
4. Document your failures
Keep a "failure journal" cataloging what you didn't understand, what assumptions were wrong, and what you learned. Review it regularly to see your growth trajectory.
My documentation of early detection engineering failures became the foundation for eventual detection strategy.
5. Publicly acknowledge knowledge gaps
Start team meetings by identifying what you don't know about the problem at hand. Model intellectual honesty for your team and see your respect grow.
In my first leadership role I opened my first meeting by saying, "Here are five areas where I need your expertise because I have gaps." It immediately changed the dynamic from performative compliance to collaborative problem-solving and helped me build trust with the team from the get go.
The Bottom Line: The Ultimate Security Leadership Skill
The most valuable security leaders aren't those who have all the answers. They're the ones who can consistently navigate uncertainty, learn new domains quickly, and make reasonable decisions with imperfect information.
This isn't a skill you develop by staying comfortable or being afraid to look "stupid". It's built through deliberate, repeated exposure to situations where you don't have all the answers - and surviving them anyway.
I've seen security leaders transform from uncertain imposters to confident guides not by eliminating their knowledge gaps, but by becoming comfortable exposing and addressing them.
The secret most security leaders won't admit: confidence doesn't come from success. It comes from surviving failure, repeatedly, until you develop the unshakable knowledge that you can figure anything out given enough time and persistence.