PocketHunt - Threat Hunting with iOS Shortcuts

Nikoloz Kokhreidze
PocketHunt is a minimalistic Threat Hunting tool for iOS. Quick lookups, threat intel and seamless API integration. Turn your iPhone into a Threat Hunting tool.

What is Threat Hunting?
Threat Hunting is one of the most exciting areas of Cyber Security. It is all about protecting your environment by identifying threats from information that you do not already know. It is that simple, and there are many methodologies on how to do it, such as Lockheed Martin's Kill Chain Approach and Diamond Model of Intrusion Analysis. While models and frameworks serve as useful guides for starting in the Threat Hunting world, real-life is sometimes quite different.
iOS Shortcuts
Apple's operating system iOS, which powers mobile devices such as iPhones and iPads, come with a native app called Shortcuts. It allows users to automate things, interact with different apps and devices, and do some scripting. Scripting is also handy for creating Shortcuts that can effectively act as tiny apps. I started using iOS Shortcuts only recently and wanted to play with automation.
I am using PiHole for home privacy and a couple of days ago started thinking about how nice it would be if I could quickly look up where my DNS requests are going to. Or get threat information about URLs that I encounter while doing research. Hmm... iOS does not have a native anti-malware solution, so why don't I also check downloaded files on my iPhone for malware?
Introducing PocketHunt
PocketHunt is a minimalistic Threat Hunting tool based on iOS Shortcuts. It allows you to quickly lookup threat information on URLs, IP addresses, and Files and generates Threat reports. PocketHunt is available at Apple's Shortcut Gallery.
Main use cases:
- Doing quick lookups for suspicious content
- Starting a hunt while commuiting or on the go
- Preparing for a bigger threat hunt by doing preliminary checks and generating reports, that can be used for later analysis
- Integrate your PocketHunt with IoT devices, Threat Intel Feeds or security products to automatically get context on the threat and/or block malicious content
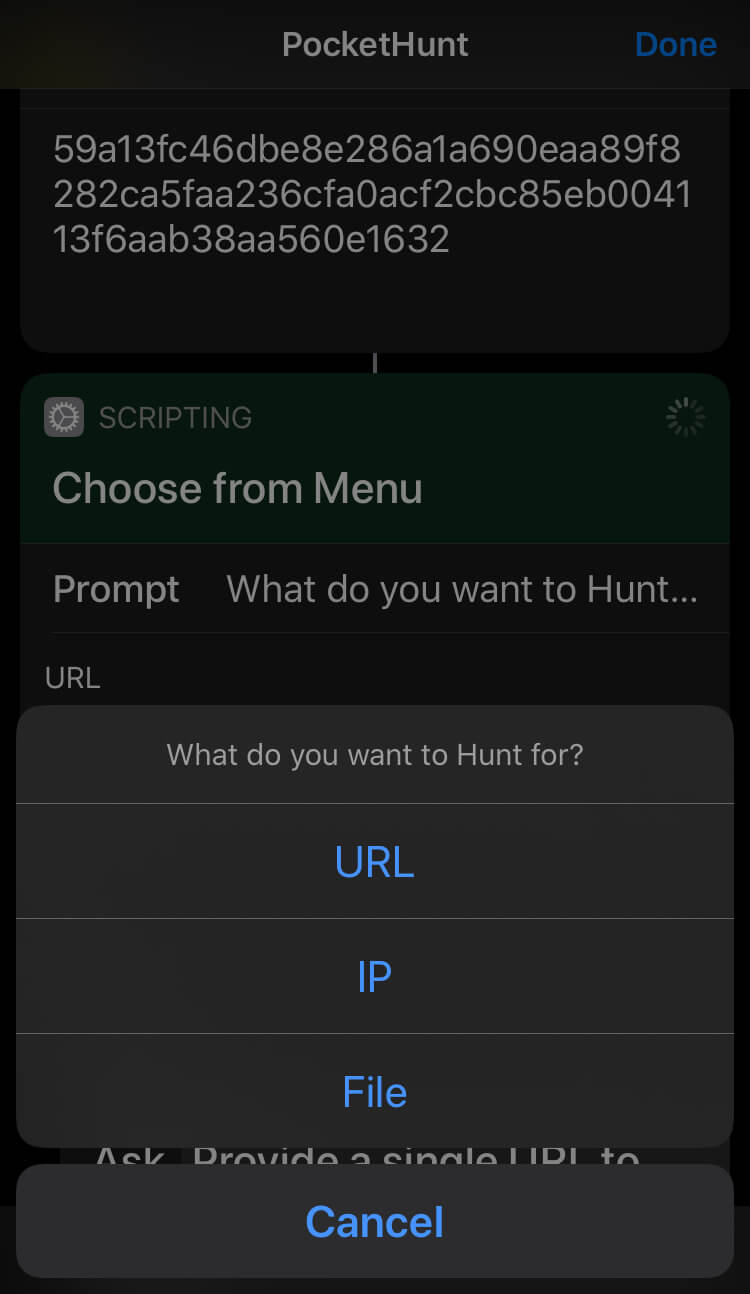
PocketHunt is fully extendable as it is powered by API integration with VirusTotal, Google Safe Browsing, AbuseIPDB, and Shodan. To make the tool work, you will need to have free/public API keys from these solutions. While shortcut has all necessary references for getting the keys from your iDevice, you can also do it by following these links: VirusTotal API, Google Safe Browsing, AbuseIPDB, Shodan.
Here are examples of malicious URL found in VirusTotal and Google Safe Browsing:
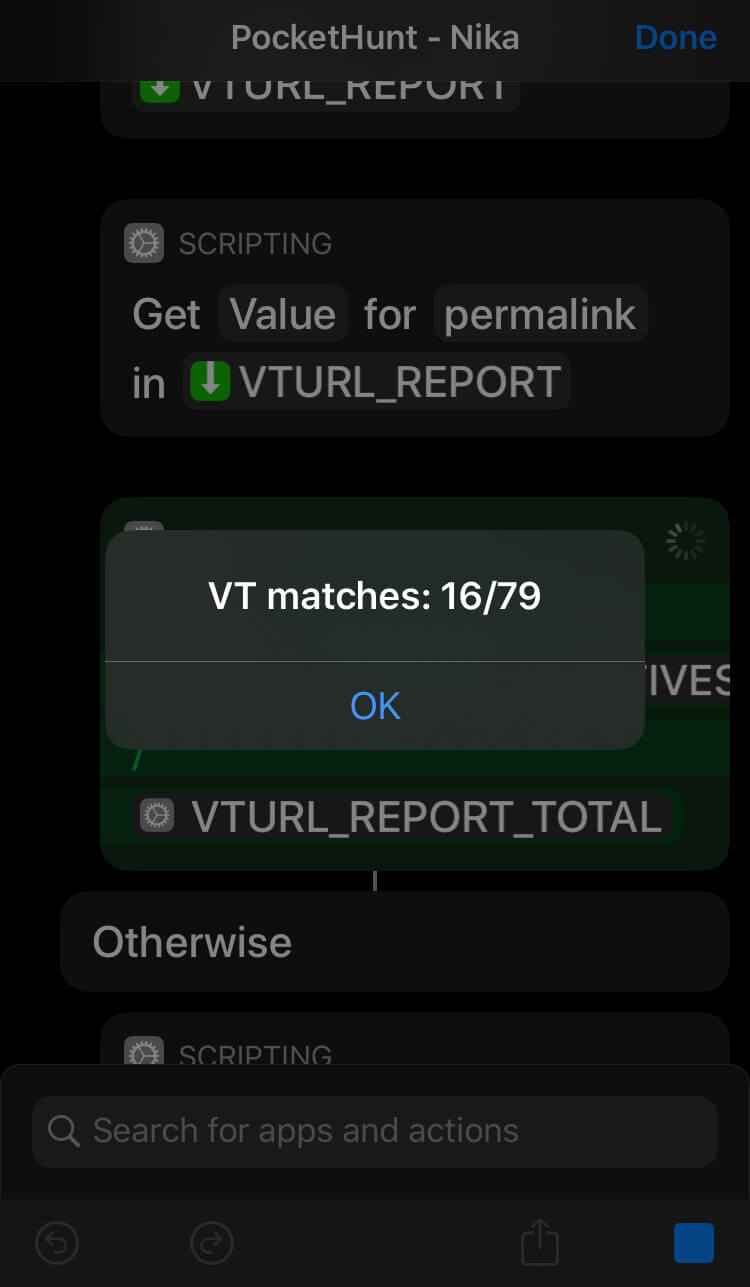
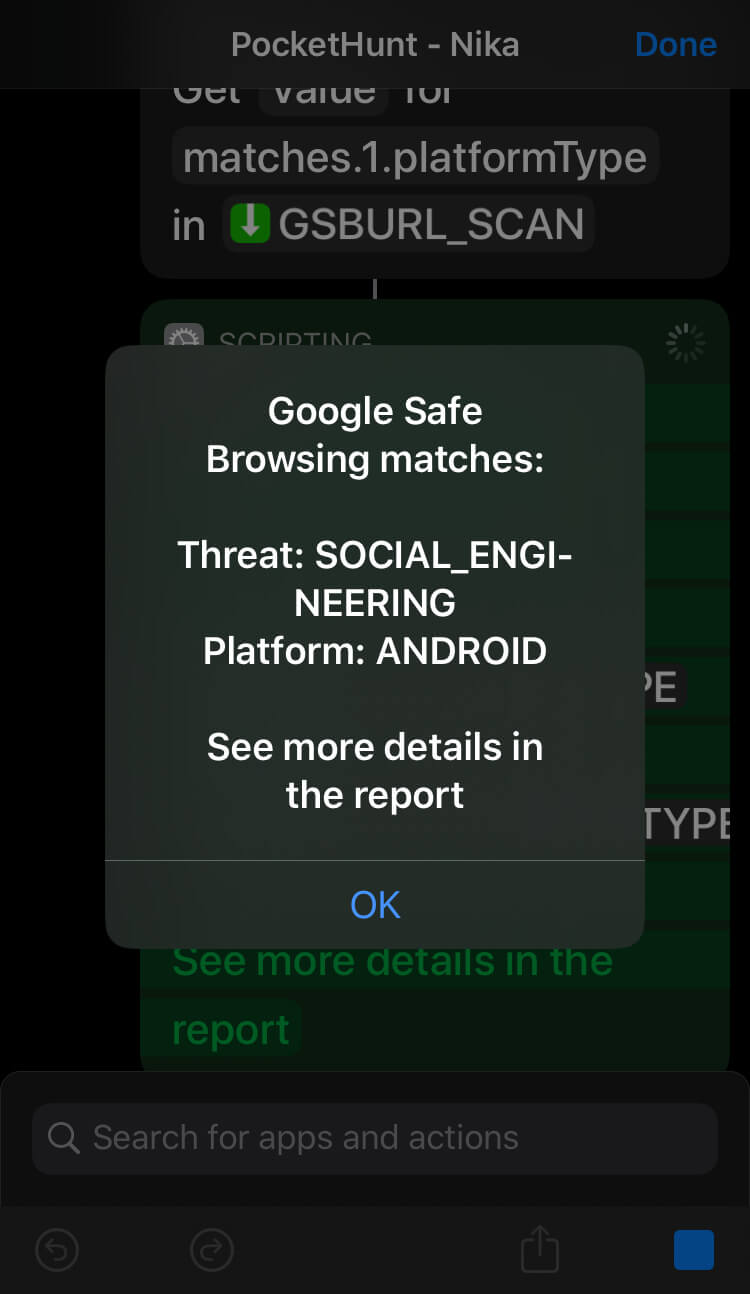
After running through the necessary steps, PocketHunt will offer to generate a report. Report is an .html file with .json data in it. So you can use the report to further parse it based on your preferences.
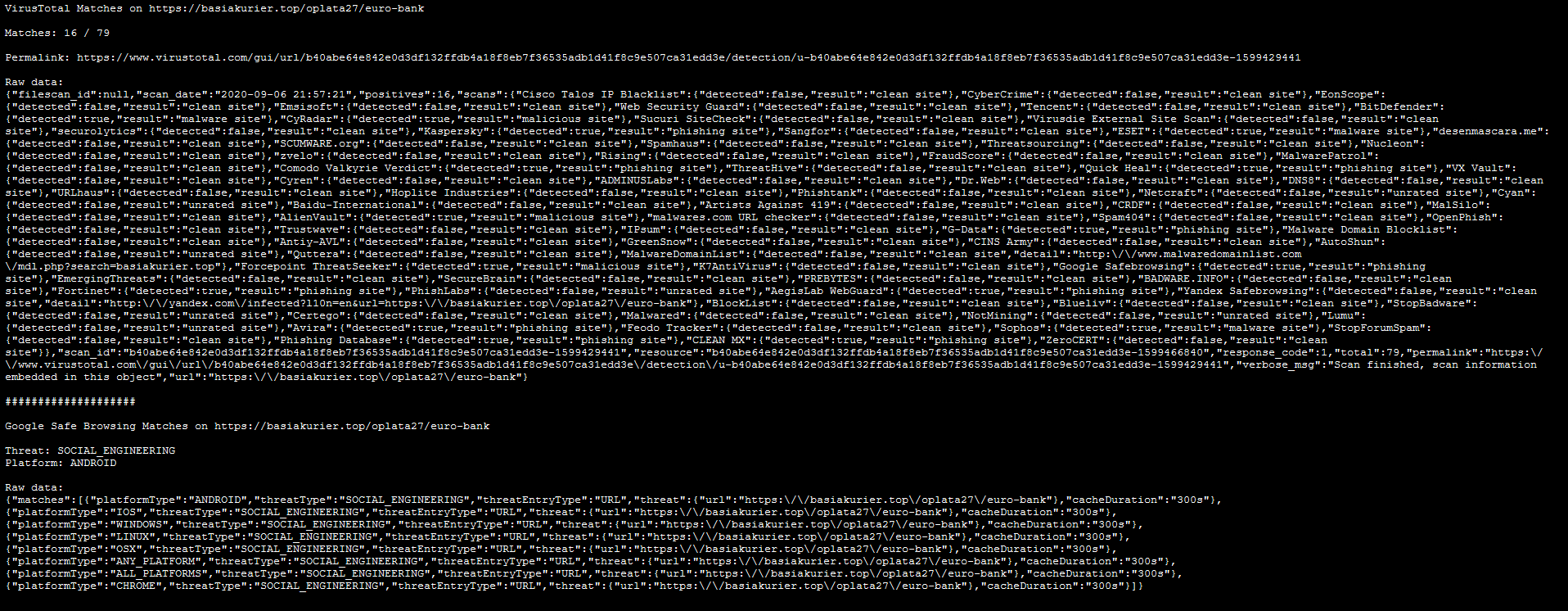
Points of Improvement
I believe there are some things that can be improved with PocketHunt,
- Beautify JSON content before putting in the report
- Onboard more tools
- Integrate with public Threat Feeds
- Support different Smart Security devices to automate blocking and protection
Obviously PocketHunt is not here to replace your Threat Hunting tools, but it can be an useful addition to your Hunting arsenal.


