Before deals close. During transitions. When boards ask.
Strategic security advisory for PE firms, boards, and executives.

You're acquiring a company and need to know what security debt you're inheriting, before it becomes your problem.
Your CISO just left and the board is asking questions you can't answer.
Security spend keeps climbing but no one can tell you what you're actually getting for it.
I've spent 13 years in these exact situations. I've seen what happens when security debt surfaces post-close. It's never pretty, and it's always expensive.
That's why I built Mandos.
Know what you're inheriting before you close.
Acquiring a company means inheriting its security debt: vulnerabilities, compliance gaps, and tool sprawl that weren't in the data room. I find what's hidden so you can negotiate with full visibility or walk away before it's too late.
Stability when security leadership is uncertain.
CISO vacancy? New leadership inheriting a mess? I step in to restructure the security function: clear reporting lines, right-sized team, priorities that match where the business is today. No long-term commitment required.
Answer the question boards keep asking: “What are we getting for this spend?”
Most security leaders can't answer that question. I can. Using market intelligence from 5,800+ security products, I show exactly what to consolidate, automate, or cut, backed by data, not guesswork.
Most advisors guess. I don't.
I built CybersecTools, the world's largest directory of 5,800+ security products. This gives me data on tool overlap, market pricing, and consolidation opportunities that other advisors simply don't have.

My approach is forged from 13 years of practical experience across banking, fintech, and global FMCG. I've seen security from every angle: from hands-on analysis at Societe Generale to leading global security programs at Mambu (Forbes Cloud 100).
Head of Security at Mambu, a Forbes Cloud 100 FinTech, leading security through hypergrowth and organizational change.
Identified €3.5M+ in annual savings for global enterprises through tool consolidation and program redesign.
5+ security integrations for major mergers, including the largest in Scandinavia and Georgia.
Due diligence on €100M+ acquisitions across 24 EEA markets for financial services and technology companies.
Choose the engagement that fits your situation.
A focused 60-minute session to unblock a specific challenge.
Best For
Quick assessment of a deal, org structure question, or tactical decision.
What You Get
Actionable recommendations you can execute immediately. Post-call, you receive the Mandos Roadmap for execution.
High Leverage
Hands-on support for M&A due diligence, leadership transitions, or program optimization.
Best For
Active transactions, CISO vacancies, or board-mandated reviews.
What You Get
Full assessment, roadmap, and ongoing advisory until the transition is complete.
Explore case studies, frameworks, and the thinking behind Mandos.
Mandos Methodology
My insights on what's actually broken in cybersecurity and how to fix it.

Stop losing million-euro enterprise deals: learn the brutal truth about how a vCISO rapidly accelerates sales and achieves ISO 27001 by focusing only on what truly closes deals.
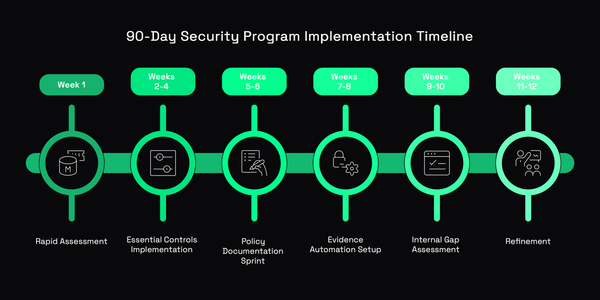
Build an ISO 27001 and SOC 2-aligned security program in 90 days to win enterprise deals. Practical guide for founders and CTOs with limited time.
Fractional CISO services are essential for growing B2B companies to win enterprise customers and grow with confidence. In this article we look at what is fractional CISO, how it works and associated costs.
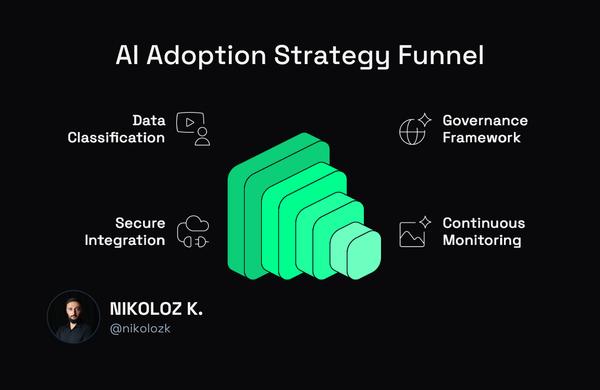
Most growing B2B companies are making the same expensive mistake with AI that they made with cloud computing 15 years ago. Here's why building your own AI infrastructure will kill your competitive advantage and what smart leaders are doing instead.
The Model Context Protocol lets AI access multiple systems simultaneously, creating security risks most organizations aren't prepared for. Learn the strategic framework needed for proper MCP governance.

Unlock your leadership potential in cybersecurity. Learn to communicate business value, build strategic networks, and embrace mentorship to bridge the gap between technical expertise and executive roles.